systemcheck - Security Check Application
Connectivity Test. Sanity Test. Update Check. And More.

Introduction[edit]
systemcheck is a script which checks numerous, important system variables. systemcheck can be run in a CLI environment (such as in terminal emulator xfce4-terminal) or via the GUI option, which has an in-built progress meter and summary notification popup of the results. The script is stored in the /usr/bin/systemcheck and /usr/libexec/systemcheck/ directories. Kicksecure is functional without the systemcheck script since it only checks the system status; it is not responsible for core settings. Nothing is compiled, and the script can be easily inspected in the source code.
The systemcheck script was inspired by browser based check websites.
Browser based check websites are useful for very specialized checks, but Kicksecure is a complete operating system. This means certain checks can be performed, otherwise a user's security might be endangered.
systemcheck allows the entire Kicksecure community to stay informed about important updates or advice, and this is particularly important for users who might not start the browser or visit the Kicksecure website regularly.
Running systemcheck[edit]
systemcheck verifies that the Kicksecure system is up-to-date and that everything is in proper working order.
Follow the steps below to manually run systemcheck and check the system status.
How-to: Manually Run systemcheck[edit]
If you are using Kicksecure for Qubes, complete the following steps. [1]
Qubes App Launcher (blue/grey "Q") → click the Whonix VM you want to check → System Check
If you are using a graphical Whonix, complete the following steps.
Start Menu → System → systemcheck
If you are using a terminal-only Whonix, complete the following step. systemcheck
Depending on system specifications, systemcheck can take up to a few minutes to complete. If everything is working as intended, the output should highlight each INFO heading in green (not red). A successful systemcheck process will have output similar to below.
Sample systemcheck Output[edit]
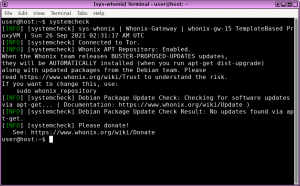
[INFO] [systemcheck] Connected to Tor.
[INFO] [systemcheck] Kicksecure APT Repository: Enabled.
When the Kicksecure team releases BUSTER-PROPOSED-UPDATES updates,
they will be AUTOMATICALLY installed (when you run apt full-upgrade)
along with updated packages from the Debian team. Please
read https://www.kicksecure.com/wiki/Trust![]() to understand the risk.
If you want to change this, use:
to understand the risk.
If you want to change this, use:
sudo repository-dist
[INFO] [systemcheck] Debian Package Update Check: Checking for software updates via apt... ( Documentation: https://www.kicksecure.com/wiki/Update![]() )
[INFO] [systemcheck] Debian Package Update Check Result: No updates found via apt.
[INFO] [systemcheck] Please donate!
)
[INFO] [systemcheck] Debian Package Update Check Result: No updates found via apt.
[INFO] [systemcheck] Please donate!
Tor Bootstrap[edit]
Tor bootstrap refers to the process of attempting to connect to the Tor network (successfully or unsuccessfully). Familiar output related to this process includes: "Tor connecting xx percent...", "Tor not connected", "Tor connected" and so on. Bootstrapping does not refer to related concepts, such as whether connections are "secure", "not secure", "anonymous" or "not anonymous".
System Checks[edit]
In all the checks below, systemcheck warnings appear if a problem is detected. Conversely, systemcheck output is otherwise quiet unless using the --verbose option. Any operating system updates, downloads or other network activity are Tor stream-isolated by default.
Table: System Checks run by systemcheck
| Check | Description |
|---|---|
| Canary | An automated Kicksecure warrant canary check is available with the --verbose parameter, see: Warrant Canary Check.
|
| Clock Source | Check if the clock source is KVMClock and warn if that is the case. [2] |
| Entropy Test | An entropy availability check confirms /proc/sys/kernel/random/entropy_avail contains no less than 112 bytes. |
| Hostname | Check if:
(Relevant inside Whonix™ only.) |
| IP Address Routing | Check if IP forwarding is disabled on Kicksecure (kicksecure).
|
| Connectivity Tests | When using --ip-test (previously called, same as --leak-tests):
Checks if |
| Log Inspection | When using the --verbose option, check if ~/.msgcollector/msgdispatcher-error.log exist and report this if confirmed.
|
| Meta-package Check | Check if the relevant meta-packages [3] are installed on Kicksecure. Also see: Kicksecure Debian Packages. |
| Network Connection | Check setup-dist has properly configured networking. |
| Operating System Updates | apt update is run through a separate APT SocksPort for stream isolation. A notification is provided whether the system is up-to-date or requires updating. |
| Package Manager | Check if a package manager is currently running and wait until the process is finished. [4] This prevents connection failures during concurrent upgrades of the Tor package. |
| Tor | Check:
|
| Repository Notification | Notifies whether Derivative APT Repository is enabled or not. |
| Stream Isolation (Whonix only) | When using --ip-test (previously called, same as --leak-tests):
A stream isolation test checks the IP addresses from (1) and (2) differ. |
| Tor Bootstrap | Tor Bootstrap Status:
|
| Miscellaneous |
|
| Virtualization Platform | Check Kicksecure is being run on one of the supported virtualizer platforms, including VirtualBox, KVM or Qubes. |
Version Numbers[edit]
Kicksecure Build Version[edit]
The version number of the Kicksecure build never changes. This is acceptable because at build time [7] the current Kicksecure version number is added to the image itself. [8]
This information is made available so systemcheck can determine which build script version was used to create that particular image.
This version number should remain static and be unaffected by updating or other issues, since it only applies to specific (usually older) versions of the build script. This is useful for diagnostic purposes and means specific build versions can be deprecated if they are too difficult or expensive to upgrade. In this case, systemcheck's Kicksecure News function would inform users about the change.
By design, the build version number cannot be upgraded. See also Update vs Image Re-Installation. It's similar to a day of birth which is also unchangeable.
Check Version[edit]
To check the current Kicksecure version, run the following command.
systemcheck --verbose --function show_versions
The output should be similar to below.
[INFO] [systemcheck] disp766 | Kicksecure | kicksecure-17-dvm DispVM AppVM | Sun 25 Apr 2021 07:13:17 AM UTC
[INFO] [systemcheck] Input Detection: INPUT_AUTO=true CLI=true GUI=false stdin connected to terminal. Using cli output. Not using gui output. Alternatively, if want to run from command line, but still use the graphical user interface for input, you could add to command line: --gui [INFO] [systemcheck] Root Check Result: Ok, not running as root. [INFO] [systemcheck] /etc/kicksecure_version: 17
Warrant Canary Check[edit]
Introduction[edit]
There are several reasons an Automated Warrant Canary Check is justified:
- Kicksecure warrant canary has limited utility if it is forgotten over time and not regularly verified.
- It is unlikely the Kicksecure warrant canary is routinely verified by the community.
- If a community member discovered the Kicksecure warrant canary verification failed, there is no effective way to notify all Kicksecure users.
Features[edit]
Table: Automated Warrant Canary Check Features
| Feature | Description |
|---|---|
| Function | Functions similar to an update check, but it establishes if Kicksecure warrant canary is still valid. |
| Security |
|
| Implementation details |
|
| Verbose parameter | During the initial deployment phase of this new feature, systemcheck will only show canary status information when using the --verbose parameter. The reason is there might be non-security related potential bugs to address:
|
| Troubleshooting | In case of issues, manually verify Kicksecure warrant canary. Also see: Whonix Warrant Canary Forum Discussion |
Disable Warrant Canary Check[edit]
This will prevent the daily Kicksecure census.
Open file /etc/systemcheck.d/50_user.conf in an editor with root rights.
Others and Alternatives
- This is just an example. Other tools could achieve the same goal.
- If this example does not work for you or if you are not using Kicksecure, please refer to this link.
sudoedit /etc/systemcheck.d/50_user.conf
Add the following content.
canary=false
Arg Max Check[edit]
Only useful in case of systemcheck GUI issues.
systemcheck --function check_arg_max
Expected result:
[INFO] [systemcheck] ERROR: ARG_MAX exceeded!
debug information:
output_func was called with too many arguments.
${FUNCNAME[0]}: output_func
${FUNCNAME[1]}: output_func_cli
${FUNCNAME[2]}: check_arg_max
${FUNCNAME[3]}: systemcheck_run_function
${FUNCNAME[5]}: systemcheck_main
${FUNCNAME[6]}: main
$0: /usr/libexec/systemcheck/systemcheck
The output message will probably be improved in the future. "ERROR: ARG_MAX exceeded!" will be rewritten to "ARG_MAX detected.".
Related[edit]
See Also[edit]
Footnotes[edit]
- ↑
Qube Manager→right-click the Whonix VM you want to check→select "Run command in qube"
Type each command below, followed by theENTERkey. xfce4-terminal-emulator systemcheck - ↑ This is only expected to affect those following the KVM instructions.
- ↑ These capture packages which depend on all other recommended / default-installed packages.
- ↑ Otherwise, eventually the system is locked or the package manager is left in a broken state. Advice is provided on what to do in such circumstances.
- ↑
Some users may wonder why it is necessary to check the IP address if the Kicksecure design ensures that the real IP cannot be leaked. Sometimes
check.torproject.orgreports false positives and fails to detect Tor exit nodes, so it is better to provide information about that possibility. This also reduces support requests and bad press. Users are welcome to investigate a Tor exit node that could not be detected, but it can be stated with high confidence that the IP address will be associated with a known Tor exit node. - ↑
Another reason to perform this check is because some users set up dangerous and/or unsupported configurations, such as:
- Using virtualizers which are entirely unsupported and untested by Kicksecure developers.
- Installing arbitrary packages on Kicksecure (
kicksecure-17). This could theoretically create leak vectors, and systemcheck is the last layer of defense against such issues.
- ↑ The time at which the image was created.
- ↑
The
dist-base-files package,
package, dist-base-files.postinst chroot script in essence runs:
chroot script in essence runs:
echo "$dist_build_version" > "$build_version_file"
- ↑ For convenience, the clearnet link that is unused by systemcheck can be previewed here: https://download.kicksecure.com/developer-meta-files/canary/canary.txt.embed.sig

- ↑ sudo -u canary signify-openbsd -V -e -p /usr/share/repository-dist/derivative-distribution-signify-key.pub -x /var/lib/canary/canary.txt.embed.sig -m /var/lib/canary/canary-unembed.txt
Unfinished: This wiki is a work in progress. Please do not report broken links until this notice is removed, use Search Engines First and contribute improving this wiki.

We believe security software like Kicksecure needs to remain Open Source and independent. Would you help sustain and grow the project? Learn more about our 12 year success story and maybe DONATE!