Whonix - Superior Internet Privacy
Jump to navigation
Jump to search
Is Whonix safer than VPNs?
| Whonix | VPNs | |
|---|---|---|
| Hidden IP address (basic) Your IP address acts as a global unique identifier which is linked to your real identity. Any website or server you are connecting to knows your IP address. Most Internet Service Providers (ISPs) keep a log of IP addresses assigned to you and when you used them. The IP address reveals your approximate physical location to any destination you connect to. | ||
|
Hidden Identity
Even if your IP is hidden, trackers can use "Fingerprinting" techniques to identify you. Hiding your identity is harder than just hiding your IP! Whonix protects from browser fingerprinting, and website traffic fingerprinting. |
||
|
No Logging
Whonix cannot log user IP addresses or activity. This is due to a
fundamental architecture design
decision to keep maximum user privacy.
Most VPNs have a policy of not storing any user data. But if they were forced to do so, they could start storing user data easily. |
|
|
|
Leak Shield
Even if a connection is tunneled, it can be hijacked inside the browser. One leaky connection already compromises the user's anonymity.
Whonix has a watertight leak shield.
Some VPN providers also have a fail-closed mechanism, however the quality varies very much and fails against malware. |
||
|
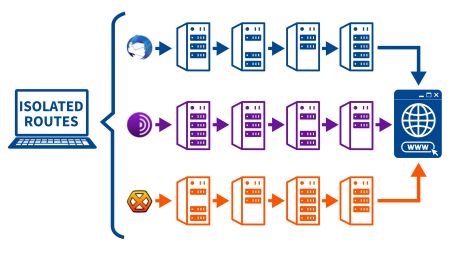
Server Relays avg.
The servers used for tunneling MUST NOT know the user. This is only possible if there are
multiple
and
independent servers
as relays on a
strict need-to-know basis
and
onion-layered encryption. Some VPN providers provide double VPN but it’s still the same provider and lacks distributed trust by design. |
3 | 1 |
|
Virus / Malware Protection
A
malware (virus)
free system
is crucial
because a lot of malware steals the user's data and identity.
Whonix is based on Kicksecure, a hardened, well documented Linux so the user is already safer. Some VPN subscriptions contain anti-malware scanners but their capability is limited. A better approach is to prevent any malware from entering the system through security hardening and knowledge. |
|
|
| Keyboard Typing Cloak Trackers can identify their targets by their keyboard typing style. Whonix prevents this kind of attack. |
|
|
| Timestamp Attack Protection Trackers can identify their targets by minimal divergence from the standard time in the network requests called time attacks. Whonix prevents this kind of attack. |
|
|
| App Stream Isolation In Whonix distinct pre-installed applications are routed through different network paths for maximum security. |
|
|
| Open Source / Freedom Whonix has a full dedication to Open Source and Freedom Software. Only some VPNs have open source elements and even less are fully Open Source. |
|
|
| Pricing |
FREE or Donation |
$5 - $20 per month |
|
Download Whonix now! |
Learn More: Whonix versus VPNs
Trusted by Security Experts
Watertight Privacy Architecture
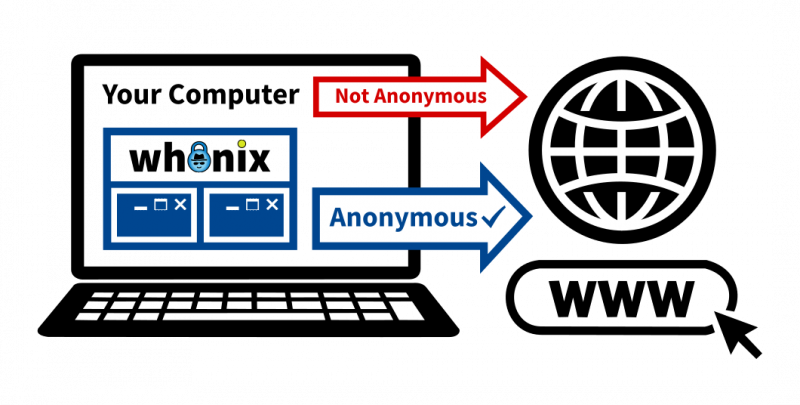
Whonix handles all your activity in a virtual machine, forcing all Internet traffic through the Tor network, providing reliable IP hiding and the strongest protection for your IP address.
Fully Featured with Advanced Security Components
Applications that are reviewed and pre-configured in Whonix
Freedom Values

We believe security software like Whonix needs to remain open source and independent. Would you help sustain and grow the project? Learn more about our 14 year success story and maybe DONATE!