Electrum Bitcoin Wallet
How-to: Use Electrum Bitcoin Wallet in Whonix


Introduction
[edit]Electrum![]()
is a popular Bitcoin wallet. According to the Electrum FAQ
![]()
:
How does Electrum work? Electrum’s focus is speed, with low resource usage and simplifying Bitcoin. Startup times are instant because it operates in conjunction with high-performance servers that handle the most complicated parts of the Bitcoin system.
Electrum does not need to download/verify the blockchain and users store their private keys locally.
This is an advantage over some other Bitcoin wallets which are affected by this: if the third-party server were ever compromised, all of the users' bitcoins could be stolen. There is also the possibility that the third-party could lose a user's private keys or walk away with them.
Warnings
[edit]See also dedicated wiki pages:
Electrum is configured by electrum upstream default to use public third party servers. If users are not using their own self-hosted electrum server (ElectrumX), consider the following quote from the electrum upstream documentation Does Electrum trust servers?![]()
:
[...]
One of the servers, arbitrarily, is selected as the “main” server.
- The client subscribes to its own addresses (nit: sha256 hashes of scriptPubKeys) so that it would be notified of new transactions touching them. It also synchronizes the existing history of its addresses. This means the client sacrifices some privacy to the server, as the server can now reasonably guess that all these addresses belong to the same entity.
- As above, confirmed transactions are verified via SPV.
- The server is trusted about unconfirmed transactions.
- The server can lie by omission. That is, it can “forget” to mention (both confirmed and unconfirmed) transactions that are relevant to the client.
- The main server is also used for fee estimates, and is trusted with those (low-high sanity limits are applied in the client)
- The main server is also used to broadcast the transactions the client makes.
[...]
There can be no blanket recommendation for all users which Bitcoin wallet should be used. It depends on:
- Technical skill.
- Personal risk assignment.
- Financial value in Bitcoin.
- Time.
- And probably other factors as well.
While Electrum has better usability (is easier to use), above warnings apply. However, for best security, the official Bitcoin client (bitcoin-qt) should be seriously considered for balances of Bitcoin representing serious financial value. For reasons, see Bitcoin Core.
Install Electrum
[edit]Installed by default in Whonix-Workstation™.
Version Numbers
[edit]Should the user wish to use a newer version of Electrum than available in the packages.debian.org electrum package![]()
since Whonix is based on Debian, the user can optionally install Electrum using the usual instructions from the Electrum website. Recommendations from the safely installing software
![]() wiki page such as Verifying Software Signatures applies. See also Install Newer Software Versions
wiki page such as Verifying Software Signatures applies. See also Install Newer Software Versions![]() .
.
It is possible to uninstall the electrum package but and uninstallation is optional if Electrum is manually installed in home folder.
See also Electrum, Manual Installation.
Start Electrum
[edit]Please refer to the official Electrum documentation![]()
for comprehensive instructions, as well as more advanced topics like Cold Storage
![]()
of private keys.
To start Electrum from start menu.
Start Menu → Internet → Electrum
To start Electrum from command line, run.
electrum
Qubes-Whonix™ users are recommended to configure a Split Bitcoin Wallet![]()
to better protect their private keys. To protect against identity correlation through Tor circuit sharing, follow the instructions below (see Stream Isolation for more information).
Electrum: First Run
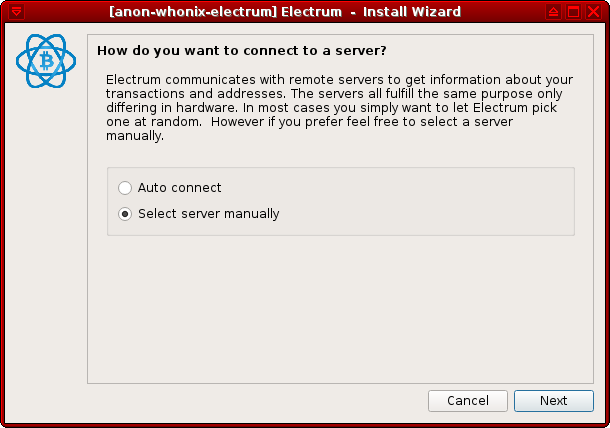
[edit]1. Configure a manual server connection.
When Electrum is started for the first time, users are met with the prompt: "How do you want to connect to a server?".
Choose Select server manually and press Next.
Figure: Server Setting
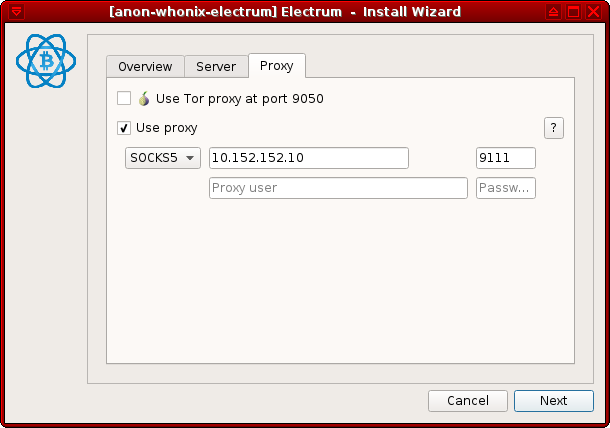
2. Change the proxy settings. This is useful for Stream Isolation.
The necessary settings are:
- Proxy:
SOCKS5 - Host:
10.152.152.10 - Port:
9111
Press Next and the application should be fully functional.
Figure: SOCKS5 Proxy Configuration
Note: If Electrum is already set up but stream isolation was not enabled, then navigate to Tools → Network in Electrum to bring up the server and proxy settings.
Uninstallation
[edit]1. Dummy dependency installation.
To avoid any issues with Whonix meta package removal, first install the dummy-dependency-electrum package.
Install package(s) dummy-dependency-electrum following these instructions:
1 Platform specific notice.
- Non-Qubes-Whonix: No special notice.
- Qubes-Whonix: In Template.
2 Update the package lists and upgrade the system![]() .
.
sudo apt update && sudo apt full-upgrade
3 Install the dummy-dependency-electrum package(s).
Using apt command line --no-install-recommends option![]() is in most cases optional.
is in most cases optional.
sudo apt install --no-install-recommends dummy-dependency-electrum
4 Platform specific notice.
- Non-Qubes-Whonix: No special notice.
- Qubes-Whonix: Shut down Template and restart App Qubes based on it as per Qubes Template Modification
 .
.
5 Done.
The procedure of installing package(s) dummy-dependency-electrum is complete.
2. Remove the electrum package.
sudo apt purge electrum
3. Done.
Removal of the electrum package has been completed.
See Also
[edit]Donations
[edit]After installing Electrum, please consider making a donation to Whonix to keep it running for many years to come.
![]() Donate Bitcoin (BTC) to Whonix.
Donate Bitcoin (BTC) to Whonix.
1HeXtk2iEXSeLr7WhVeCmWgHDw3oE2PKTY
Footnotes
[edit]
We believe security software like Whonix needs to remain open source and independent. Would you help sustain and grow the project? Learn more about our 13 year success story and maybe DONATE!