Reliable IP Hiding - with Whonix - The All Tor Operating System
Whonix is The Everything Tor OS
Reliable IP Hiding
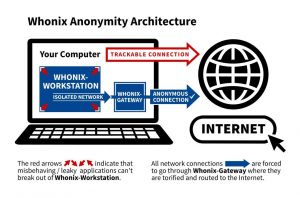
[edit]All internet traffic is routed through the Tor anonymity network. No exceptions. Whonix is the "All Tor Operating System".
Whonix handles all your activity in a virtual machine and forces all Internet traffic through the Tor network to provide the strongest protection of your IP address.
All traffic originating from Whonix-Workstation™ and Whonix-Gateway™ is routed to the Tor software.
For technical details, click on "Learn More" on the right side.
- Traffic from Whonix-Gateway also routed over Tor: Starting from Whonix version
0.2.1, traffic from Whonix-Gateway is also routed over Tor. This approach conceals the use of Whonix from entities monitoring the network. - Gateway's own traffic not essential for anonymity: To preserve the anonymity of a user's Whonix-Workstation activities, it is not essential to route Whonix-Gateway's own traffic through Tor. (Note: The gateway is mainly a tool that helps route traffic; it does not typically contain personal activity data.)
- DNS configuration on Whonix-Gateway has limited impact: Altering DNS settings on Whonix-Gateway in
/etc/resolv.confonly impacts DNS requests made by Whonix-Gateway's applications that utilize the system's default DNS resolver. (DNS is like the internet's phonebook - it translates website names to IP addresses.) By default, no applications on Whonix-Gateway that generate network traffic use this default resolver. All default applications on Whonix-Gateway that produce network traffic (like apt, systemcheck
, sdwdate) are explicitly configured, or forced by uwt wrappers, to use their dedicated Tor
SocksPort(refer to Stream Isolation). - Whonix-Workstation DNS requests handled via Tor: Whonix-Workstation's default applications are configured to use dedicated Tor
SocksPorts(see Stream Isolation), avoiding the system's default DNS resolver. Any applications in Whonix-Workstation not set up for stream isolation - such asnslookup- will use the default DNS server configured in Whonix-Workstation (through/etc/network/interfaces), which points to Whonix-Gateway. These DNS requests are then redirected to Tor'sDnsPortby the Whonix-Gateway firewall. (This ensures DNS lookups still go through Tor even if they use the default method.) Changes in Whonix-Gateway's/etc/resolv.confdo not influence Whonix-Workstation's DNS queries. - Tor process traffic allowed direct internet access: Traffic produced by the Tor process, which by Debian's default operates under the account
debian-torand originates from Whonix-Gateway, can access the internet directly. This is permitted because the Linux user accountdebian-toris exempted in the Whonix-Gateway Firewall and allowed to use the "regular" internet. (This is necessary for Tor to establish its connections.) - Tor mostly uses TCP traffic: As of Tor version
0.4.5.6(with no changes announced at the time of writing), the Tor software predominantly relies on TCP traffic. (TCP is a common protocol used for stable internet connections.) For further details, see Tor wiki page, chapter UDP. For DNS, please refer to the next footnote. - Tor's DNS independence and exceptions: Tor does not depend on, nor use, a functional (system) DNS for most of its operations. IP addresses of Tor directory authorities are hardcoded in the Tor software by Tor developers. (That means Tor knows important addresses in advance and doesn't need to look them up.) Exceptions include:
- Proxy with domain name: Proxy settings that use proxies with domain names instead of IP addresses.
- Pluggable transport domain resolution: Some Tor pluggable transports, such as meek lite, which resolve domains set in
url=andfront=to IP addresses, or snowflake's-front.
No additional user configuration is required. (Using helper utilities such as torsocks, torify, or configurations such as Tor SocksPorts is not necessary for IP concealment but can be useful for Stream Isolation.)
This is made possible by Whonix's Architecture.
For technical details on how this is accomplished, readers can refer to the Whonix technical introduction.
- See Whonix against Real Attacks for a list of many past anonymity attacks where Whonix kept its users safe.
- See Whonix uses multiple security layers for reasons why leaks are highly unlikely.
- See this page Leak Tests for testing for IP/DNS leaks generally.
- If you think you might have found a leak or something unusual, see Leaks.
- See Security Reviews and Feedback for a list of notable reviews and feedback about the security of Whonix.
- See System Audit
 for how users (cannot) verify the system is configured as intended.
for how users (cannot) verify the system is configured as intended. - This might also relate to the question "How secure is Whonix?" → Technical Introduction
None of the Leak Testing Websites / Browser Tests running inside Whonix are able to determine the real external clearnet IP address, regardless of whether plugins, flash, and/or java are activated.
Given that there have been no known instances of IP leaks attributed to Whonix bugs throughout its 13 years of history, it can be reasonably inferred that Whonix offers a reliable feature for IP address concealment.
Fail-Closed Mechanism
[edit]Whonix's architecture enables the "torification" of applications that lack built-in proxy support. This means users can install and use custom applications or modify their desktop environment without risking IP address leaks.
All application traffic is either routed through the Tor network or entirely blocked. This includes a wide variety of software such as web browsers, Browser Plugins, E-Mail clients, chat applications, VoIP, SSH, Remote Administration tools, VPN clients or proxy software, cryptocurrency wallets or relays, servers, and many other types of applications.
This fail-closed design is universally applicable and even extends to Other Operating Systems that are connected through Whonix-Gateway.
See also Features, Advantages, Use Cases - Whonix chapter Tor Network / Torification / The Everything Tor OS.
Beyond IP Hiding
[edit]Hiding your identity is harder than just hiding your IP.
Concealing one's identity involves far more complexity than simply hiding an IP address. The idea of relying solely on IP address anonymization dates back to the 1990s and is no longer sufficient. Modern adversaries use a wide range of advanced Data Collection Techniques that can bypass IP-based protections entirely. These techniques are demonstrated in various Browser Tests, such as the Fingerprint.com Demo![]()
. Notably, as referenced in "12% of the top 500 websites employ Fingerprint.com's services".
For further discussion, see IP Hiding is an Outdated Threat Model.
To protect user anonymity more comprehensively, Whonix provides Full Spectrum Anti-Tracking Protection and is much safer than VPNs![]()
(see the full Whonix versus VPNs comparison).
Footnotes
[edit]
We believe security software like Whonix needs to remain open source and independent. Would you help sustain and grow the project? Learn more about our 13 year success story and maybe DONATE!















