Encrypted Email with Thunderbird

Encrypted Anonymous Email with Thunderbird
Introduction
[edit]Due to the complexity of software in the past, one of the most underutilized forms of protection for users is email encryption. However, it is now easier to take advantage of encrypted email via the use of Thunderbird (Mozilla's email client), which includes a built-in OpenPGP![]()
encryption program.
Thunderbird in Whonix comes with anonymity, privacy and security settings pre-configuration through the pre-installed anon-apps-config![]()
package. [1]
The following guide provides a higher security and privacy standard than relying upon online services such as ProtonMail or Tutanota, that promise "encrypted email" in transit or storage. Online systems can still be broken by an attacker capable of exploiting JavaScript flaws or undermining certificate authorities that provide encryption certificates for websites; see Webmail. Further, online providers can be hacked or coerced by adversaries to provide access for extended periods.
To minimize these risks and improve security, the following guide uses a suitable Desktop Email Client instead of webmail, paired with strong, end-to-end encryption that protects the contents so it can only be read by the intended recipient. Further, a strong encryption key-pair is created so the user has strict control over the private key, which is stored securely. Keep in mind this method does not make email infallible -- advanced adversaries can easily penetrate Internet-facing endpoints of targets with today's cutting-edge surveillance and offensive systems. Also, mistakes or poor security practices on behalf of the email recipient can inadvertently lead to disclosures of plaintext.
Overview
[edit]The following guide provides steps to:
- Install the Thunderbird email client.
- Visit your suitable email provider website anonymously via Tor Browser (Preferable if it support onion hidden services).
- Create your login password and store the credentials in KeePassXC

(optional). [3]
- Setup the new email account: Thunderbird account settings, and enforce connections to the email provider's Onion Service.
- Create an OpenPGP encryption key pair and revocation certificate using the Thunderbird Setup Wizard.
- Encrypt and store the revocation certificate securely.
- Configure Thunderbird preferences for greater security and anonymity.
- Configure additional OpenPGP preferences.
- Key management: import GPG public keys.
- Export the public key to a GPG key server (optional).
- Prepare an email signature with the public GPG key ID and fingerprint (optional).
- Compose and send a test encrypted email
- Open an encrypted email received in Thunderbird.
Warnings
[edit]Operational security is imperative to maintain the integrity of properly encrypted email. Consider the following scenarios which would allow an adversary access to the plaintext or other metadata that might help deanonymize a user:
- Even if all email sent to a recipient is encrypted, if the recipient fails to encrypt the email response, then adversaries will be able to read the message and likely a quote of the original one sent.
- The names of email recipients cannot be encrypted and are therefore visible to adversaries. The subject line and references email header will also be visible in the following configuration.
- There are several different types of metadata
 that can be harvested from email, depending on how it is used. Therefore, users must be careful when relying on email for sensitive communications.
that can be harvested from email, depending on how it is used. Therefore, users must be careful when relying on email for sensitive communications.
Glossary
[edit]Terms that are commonly used in reference to email encryption are outlined below.
| Term | Description |
|---|---|
| Key Pair | A pair of asymmetric keys, commonly known as public and private keys. |
| Public Key | The half of a key pair that is distributed publicly and used for encrypting. |
| Private Key | The half of a key pair that is kept secret, and is used for decryption. |
| Key Server | A server or website used for the distribution and verification of public keys. |
| Integrity | A verification that the enclosed contents have not been tampered with in transit. |
| Confidentiality | A verification that the enclosed contents are unreadable, except for the intended recipient. |
| Authentication | A verification that the person who is sending / signing is who they say they are. |
| Non-repudiation | Assurance that nobody, including the author, can dispute the origin of the message itself. |
| Asymmetric Keys | Commonly referred to as a 'keypair'. It is two separate keys: one public, one private. |
| Symmetric Keys | Symmetric encryption depends on using a password to encrypt the single key used for both encryption and decryption. |
Install the Thunderbird Email Client
[edit]For users that would like to learn more about Thunderbird refer to the official support page![]()
. However, modifications should not be made to Thunderbird unless you know what you are doing.
The Thunderbird email client can be installed from the terminal using APT secure package manager.
In Whonix-Workstation™ (whonix-workstation-18 Template Qubes-Whonix™) konsole, run.
sudo apt install thunderbird
Note: If the following output appears Thunderbird is already installed and no further action is needed.
Reading package lists... Done Building dependency tree Reading state information... Done thunderbird is already the newest version.
Create a New Email Account with Tor Browser
[edit]Choose an Appropriate Email Provider
[edit]First and foremost, there are multiple email providers that users can choose from. For the purpose of this tutorial, danwin1210.de is used as an example. This is not an endorsement (terms of service non-endorsement) for danwin1210.de. No e-mail providers are explicitly recommended by the Whonix team. The Whonix project is not an e-mail provider review project that recommend specific e-mail providers. Refer to the list of Anonymity Friendly Email Provider List for possible alternatives. If problems are experienced with danwin1210.de, refer to the list of providers by The Tor Project![]()
, Whonix or JonDonym
![]() .
.
At the time of writing, danwin1210.de is one of the few free and reliable email providers offering POP3 email access through an .onion address, which does not require additional verification details to register an account. You will have 25MB of disk space available for your emails. For more details regarding the features and offerings of danwin1210.de, visit http://danielas3rtn54uwmofdo3x2bsdifr47huasnmbgqzfrec5ubupvtpid.onion/![]() .
.
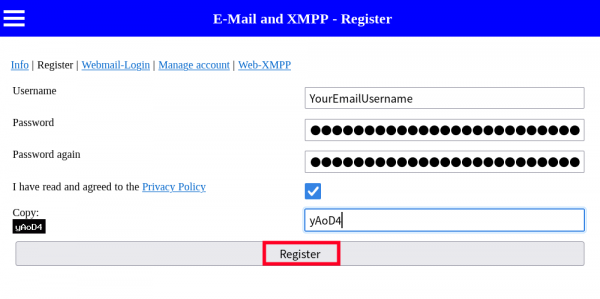
Registration Steps
[edit]1. Create an email account name and password for the mail provider.
- When the page opens, open up KeePassXC and create an account and password entry for your new email account. Alternatively, write it down at home and store it in a safe place.
- When finished creating your Email Name/Username and password in KeePassXC, Follow these steps:
Figure: Email Registration
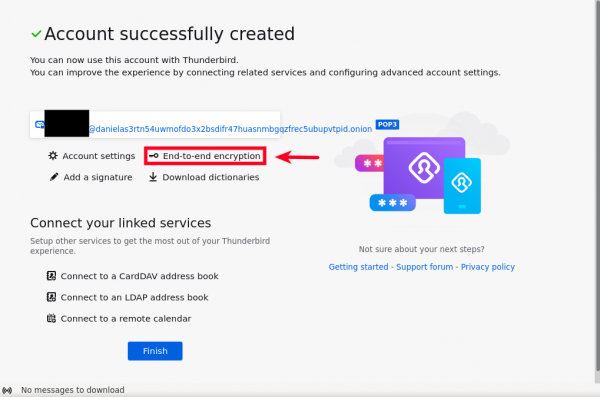
2. Confirm successful creation of the anonymous account.
Figure: Account Confirmation
3. Close Tor Browser
Since the email account is created, Tor Browser can be closed.
Setup the New Email Account in Thunderbird
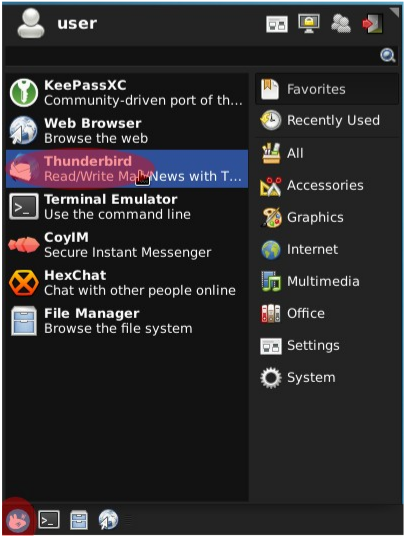
[edit]1. Open Thunderbird.
- Non-Qubes-Whonix:
Click the start menu button→Search and select Thunderbird - Qubes-Whonix:
Click the blue "Q" button→Click on anon-whonix→Select "Thunderbird"
Figure: Thunderbird Email Client (Non-Qubes-Whonix)
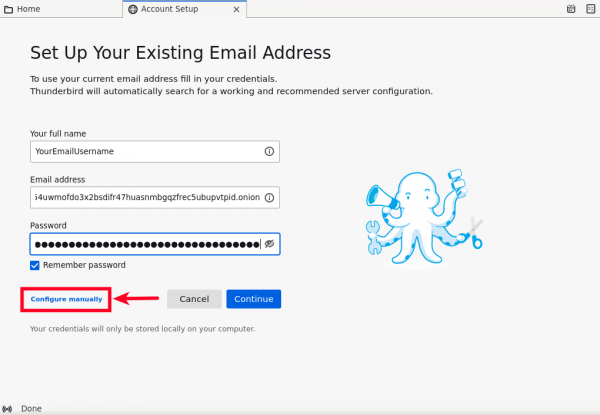
2. Set up the Email Account.
The first window that will appear upon running Thunderbird for the first time will prompt you to "Set Up an Existing Email Account." Follow these steps:
- Type the alias/username that you created in the field "Your name." This will appear next to your email address in emails you send to others.
- Type the
danwin1210.deonion email address you just created into the field "Email address." exampleyouremailusername@danielas3rtn54uwmofdo3x2bsdifr47huasnmbgqzfrec5ubupvtpid.onion- In case you will use the clearnet version then your email going to be
youremailusername@danwin1210.de
- In case you will use the clearnet version then your email going to be
- Paste your newly created password.
- Finally, Tick "remember password" (Better user friendly method) and click the "Configure Manually" button.
Figure: Email Account Set Up
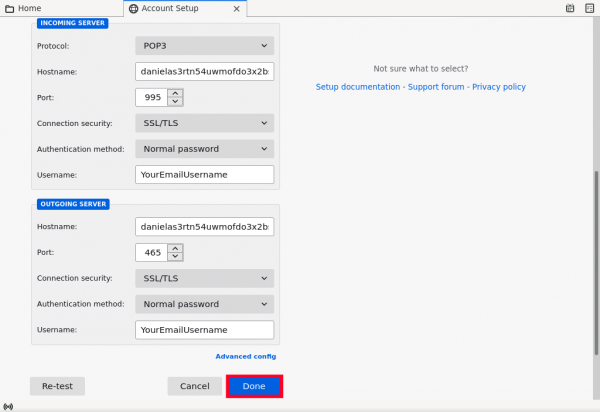
3. Configure Email Incoming (POP3) and Outgoing (SMTP) Connection.
You need to configure Thunderbird to connect to the hidden server (onion service) of danwin1210.de. The fields you need to change are:
- Protocol: Pick POP3, avoid the usage of IMAP as this makes you more exposed into the internet (as it require persistent connection to function properly), drain your account limited capacity storage (which way much less than your own operating system available storage).
- Type
danielas3rtn54uwmofdo3x2bsdifr47huasnmbgqzfrec5ubupvtpid.onionin the field next to "Hostname" - Type
995into "Port" field. - Choose "SSL/TLS" for "Connect security".
- Avoid the usage of STARTTLS

- Some email (onion) providers doesnt add TLS/SSL for their onion domain, if so then its fine to choose "None" as an option because all communications to onion domains are encrypted. Therefore, your password is not transmitted insecurely (but in our case
danwin1210.deis using self signed TLS/SSL certificate).
- Avoid the usage of STARTTLS
- Choose "Normal Password" for "Authentication Method".
- In case there was no TLS/SSL support for your email onion service its fine to choose "Password, transmitted insecurely" (but in our case
danwin1210.deonion service support TLS/SSL).
- In case there was no TLS/SSL support for your email onion service its fine to choose "Password, transmitted insecurely" (but in our case
- Type the email user name you have chosen earlier into the field next to "UserName".
Figure: Thunderbird Server Configuration
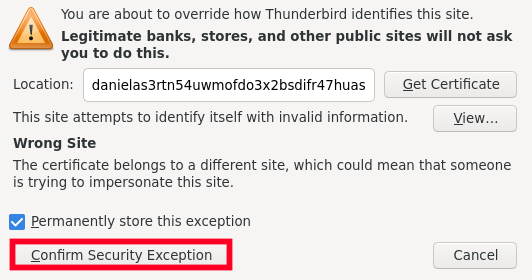
- Press on "Confirm Security Exception" its safe to confirm it because this is self-signed certificate
Figure: Confirm Self-Signed TLS/SSL inside Thunderbird
Your account is now successfully connected with thunderbird.
Create an OpenPGP Key Pair and Revocation Certificate
[edit]There are two methods for creating an OpenPGP key pair and revocation certificate -- using either the Thunderbird OpenPGP Setup Wizard, or manually creating them from the command line. The easier Thunderbird OpenPGP method is outlined below, but the manual creation of stronger keys from the command line is recommended for advanced users or those at high risk.
Create an OpenPGP Key Pair by Thunderbird
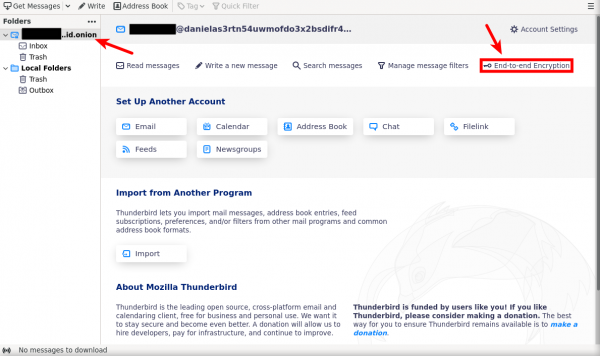
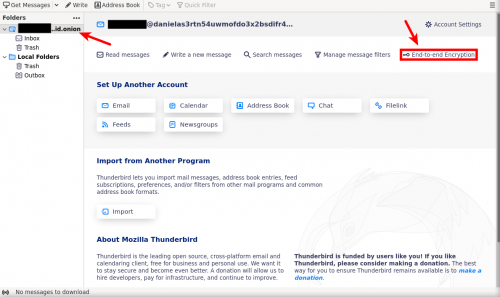
[edit]- After successfully linked your account with thunderbird click on "End-to-end encryption".
- If you missed that, you can press on your email then "End-to-end encryption" option will show up.
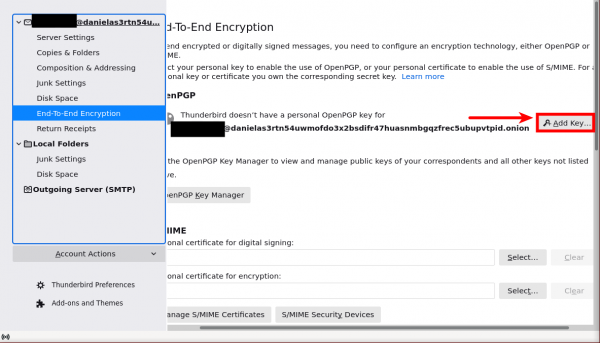
- Press on "Add Key..." Option.
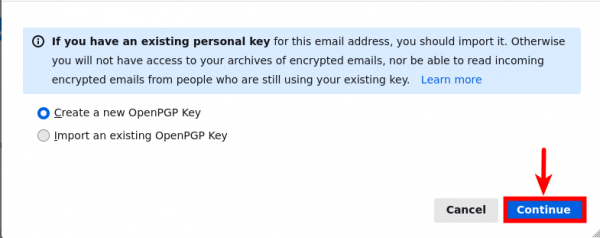
- Since we are creating new fresh keys, choose "Create a new OpenPGP Key" then press "Continue".
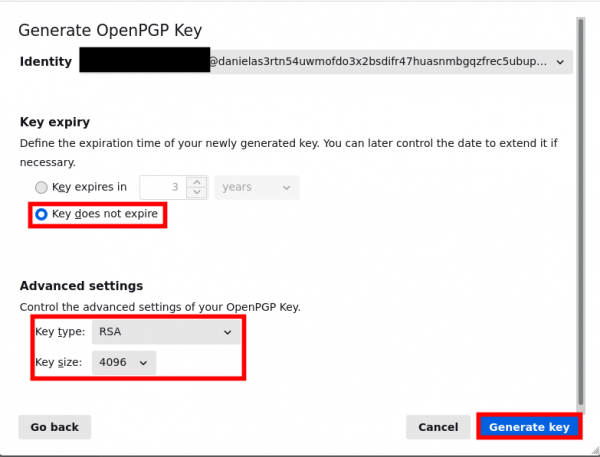
- For better usability we gonna choose "Key does not expire" option, though you can later change that to whatever suits you.
- We are going to choose the most common key type and size options which are RSA with 4096 (Other option provided by thunderbird is ECC).
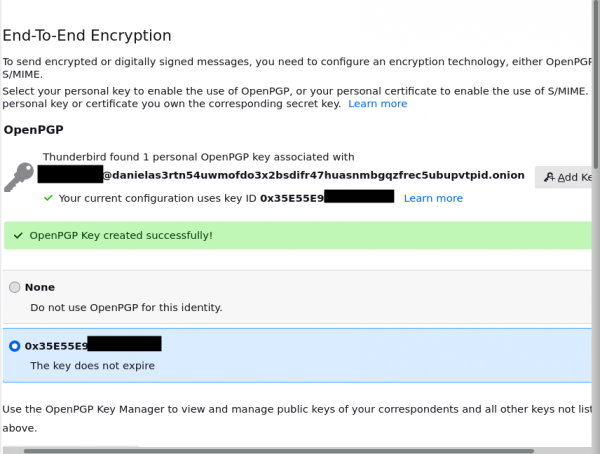
- Make sure to read the info message then press on "Confirm".
- After waiting for short time your keys are now successfully created for your account.
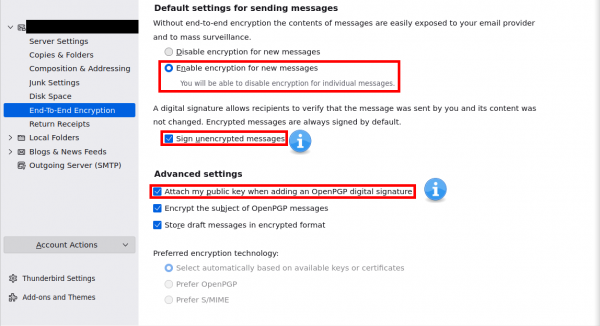
- Scroll down in the same page then choose "Enable encryption for new messages" (This will require to have recipient OpenPGP key otherwise messages wont be encrypted).
- "Sign unencrypted messages" and "Attach my public key when adding an OpenPGP digital signature" are for better authenticity and usability but they are left to the user to decide.
- Make sure these options are ticked "Encrypt the subject of OpenPGP messages" and "Store draft messages in encrypted format"
Export and Store your Keys
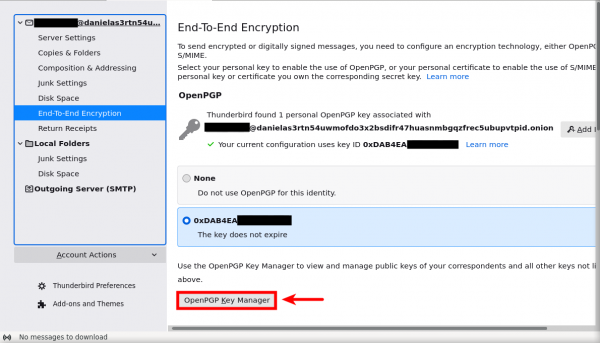
[edit]1. Go to "End-to-end encryption".
2. Then press on "OpenPGP Key Manager".
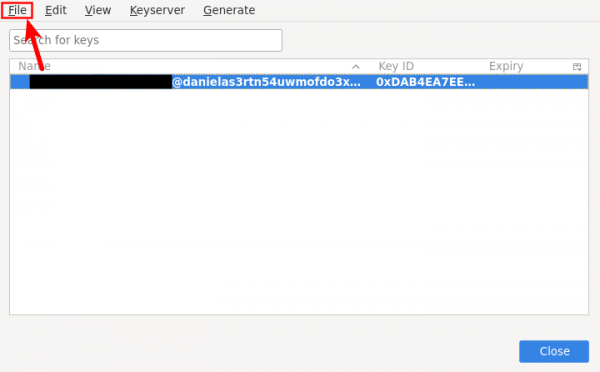
3. Then press on your email (highlight it) if there is more than one email then "File".
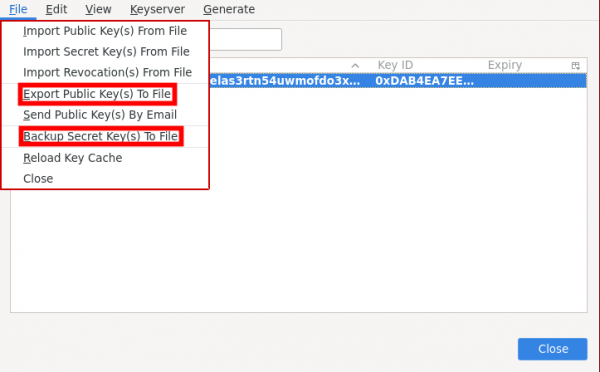
4. Then Export your Public and Secret Keys for backup as your public key used by the recipients to encrypt messages and secret key used for decrypting messages (Make sure to save them in a secure place, otherwise anybody can decrypt and read your encrypted emails if your secret key lost).
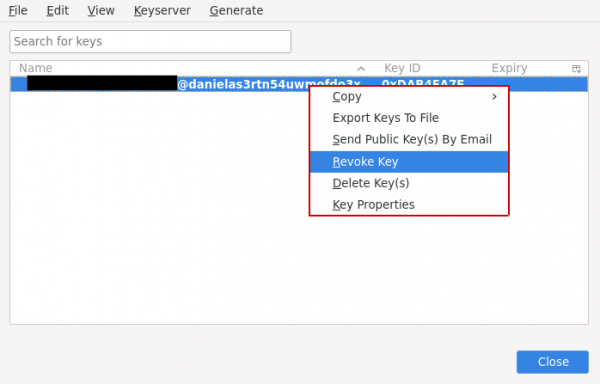
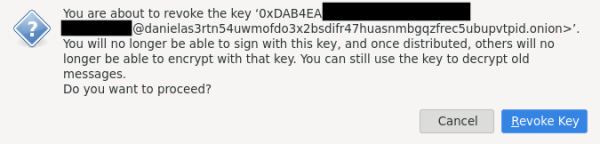
5. At the moment thunderbird doesn't give UI way to export your revoke key [6] [7], But you can revoke your key from "OpenPGP Key Manager" (Read the warning message, don't proceed unless you really want to get rid/change of your current key).
Encrypt the Revocation Certificate
[edit]The revocation certificate can be encrypted and stored in the persistent storage directory. The GPG revocation certificate can be used to revoke the public encryption key that is added to key servers, even if access to the GPG secret key is lost or the password is forgotten.
If an attacker accesses the GPG revocation certificate, they can revoke the keys. Encrypting the GPG revocation certificate with a passphrase will protect against this action.
At the moment of writing there isn't a UI/graphical friendly way of doing this through thunderbird [8].
As encryption tool you can use zulucrypt![]()
as an example (installed by default in Whonix).
Final Thunderbird and Email Account Settings
[edit]Configure Thunderbird Folders from Account Settings
[edit]1. Go to your "Account Settings"
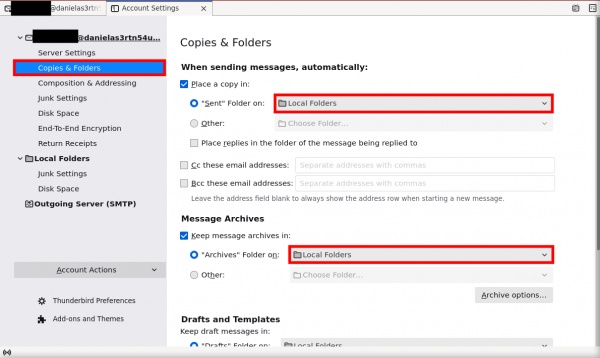
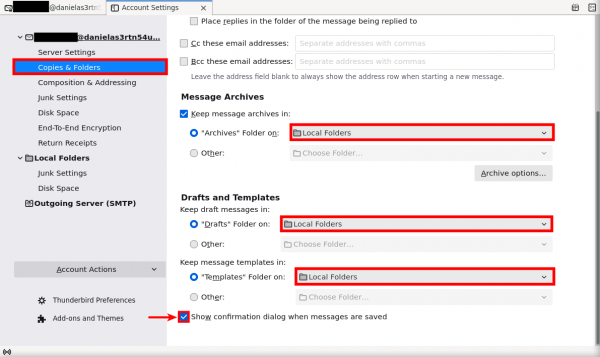
2. Click on "Copies & Folders" in the left column. Each option to change is highlighted in red in the figure below:
- In the pull down menu next to "Sent Folder on", select "Local Folders."
- In the pull down menu next to "Archives Folder on", select "Local Folders."
- In the pull down menu next to "Drafts Folder on", select "Local Folders."
- In the pull down menu next to "Templates Folder on", select "Local Folders."
- Check the box next to "Show confirmation dialog when messages are saved."
Figure: Folder Configuration
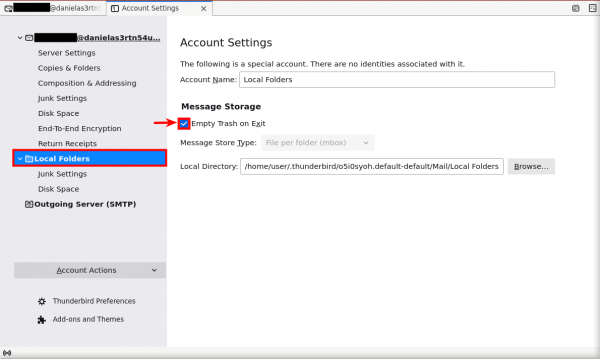
3. (Optional) Empty Thunderbird trash on exit.
Click on "Local Folders" in the left column. Then, check the box next to "Empty trash on exit."
Figure: Empty Local Folders
General Thunderbird Settings
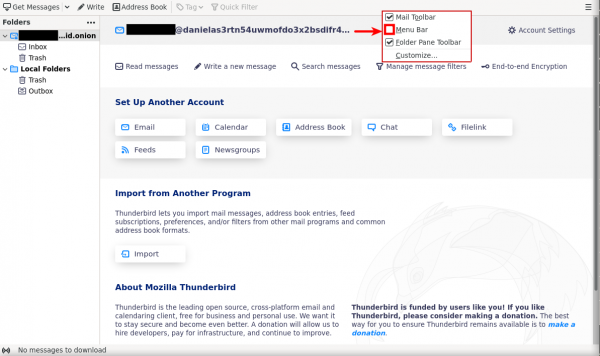
[edit]1. Set the Menu Bar.
- Right-Click in the empty top bar of thunderbird.
- Then tick "Menu Bar"
Figure: Thunderbird Menu Bar
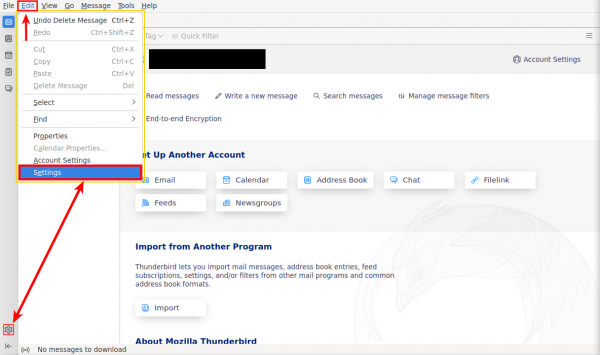
2. Access Thunderbird Settings.
- In the menu bar, click on "Edit" and then click "Settings".
- Or press the cog icon which will lead you to "Settings" as well.
Figure: Thunderbird Preferences
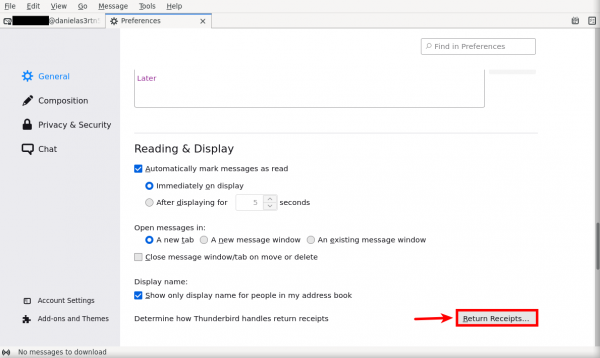
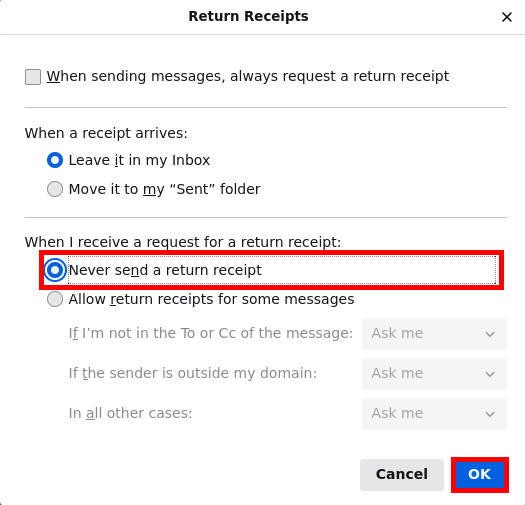
3. Disable the return receipt function.
- Scroll down then press on "Return Receipts..."
- In the next window that appears, mark the circle next to "Never send a return receipt." Then, click the "OK" button.
Figure: Disable Return Receipts
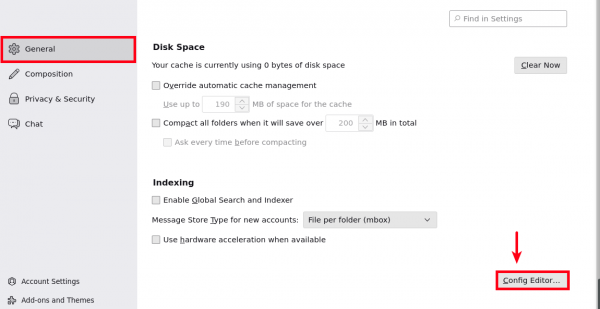
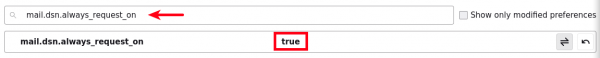
4. (Optional) Receive confirmation mail when message sent to the recipient
- From "General" scroll down to "Config Editor..."
- Search for
mail.dsn.always_request_on - Double click on it to turn it from
falsetotrue - You will receive "Successful Mail Delivery Report" after sending successful message.
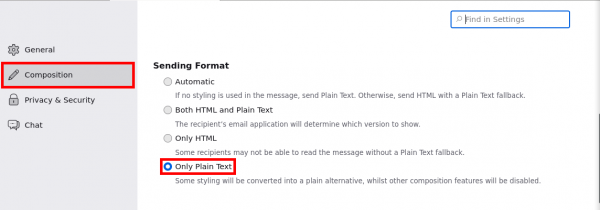
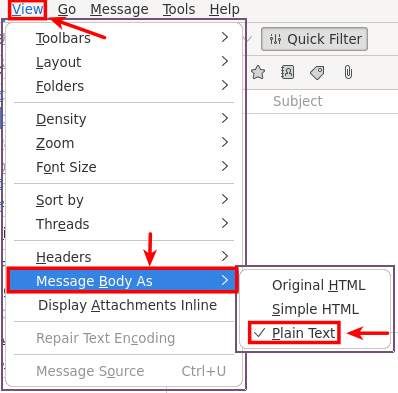
5. Send and receive plain text messages.
- One of Efail

prevention is to avoid HTML messages all together
- Click on "Composition" then choose "Only Plain Text".
- From Menu Bar click on "View" then "Message Body As" then tick "Plain Text".
Figure: Plain Text Messages
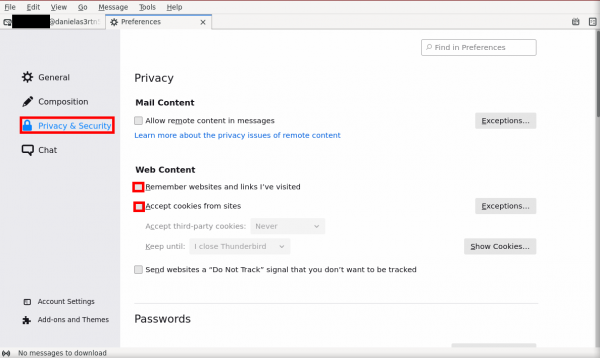
6. Disable website history and Sites cookies.
- Next, click the "Privacy & Security" button. Then, untick the box next to "Remember websites and links I've visited" and "Accept cookies from sites".
Figure: Modify Privacy Settings
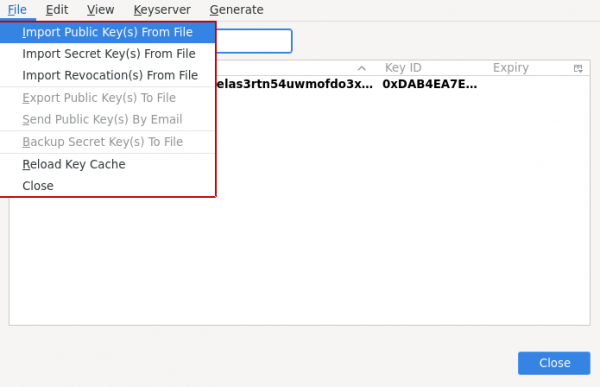
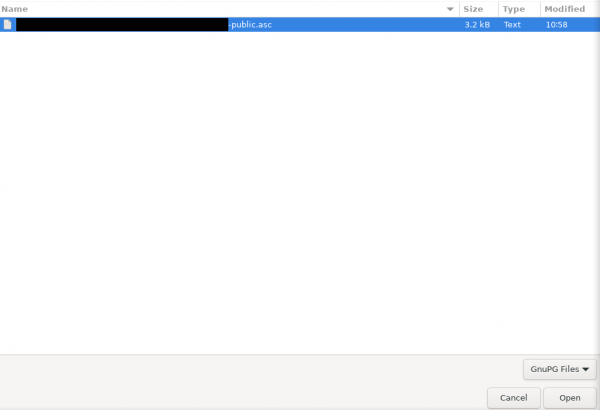
Import Public Keys (From File)
[edit]Import GPG public key of an intended email recipient keys into Thunderbird:
- Go to "End-to-end encryption"
- Then press on "OpenPGP Key Manager"
- Go to "File" then choose "Import Public Key(s) From File"
- Go to the path that where the public key is located and double-click it
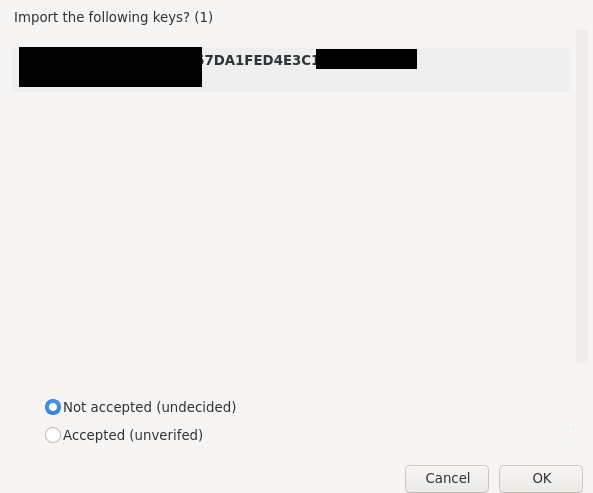
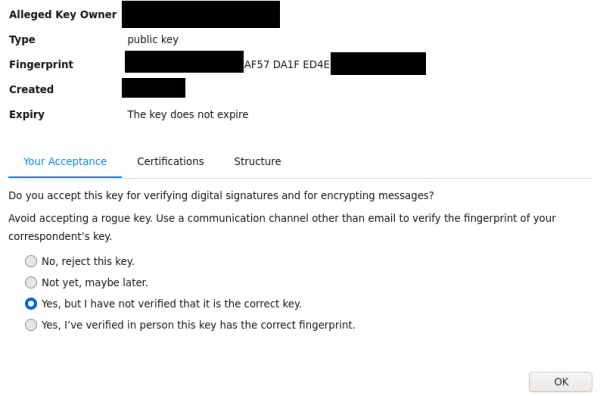
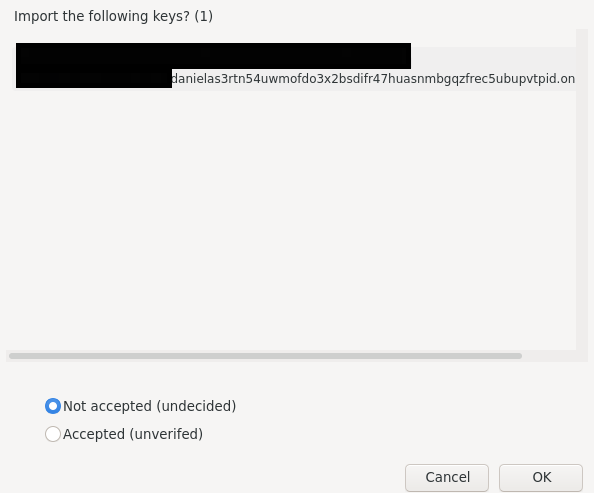
- It will show you key fingerprint, if you can verify/sure that the person with this fingerprint match what you have added then press on "Accepted (unverified)" otherwise use the default "Not Accepted (Undecided)"
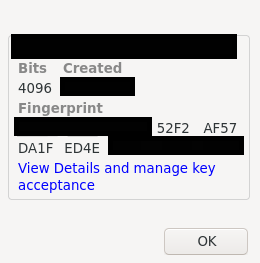
- Key is now imported successfully, if you want to change the acceptance level press on "View Details and and manage key acceptance"
- See which option do you prefer to choose for the added keys
Compose and Send Encrypted Email
[edit]1. Compose a new email message.
- Press on "Write"
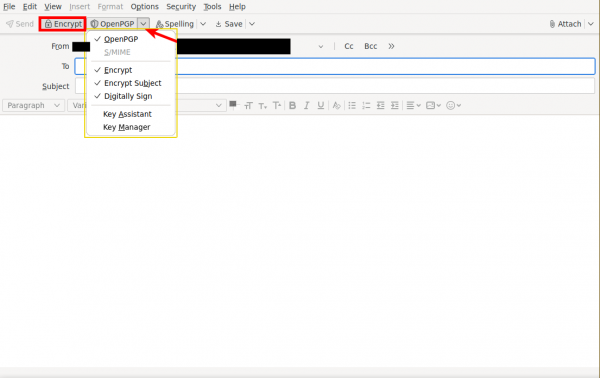
2. Send the email message.
- Make sure padlock "Encrypt" is active.
- Press on the down arrow near "OpenPGP" then make sure "Encrypt" and "Encrypt Subject" are ticked.
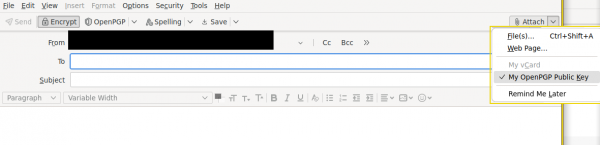
- Optional For the authenticity and easiness:
- Tick "Digitally Sign".
- Tick "My OpenPGP Public Key" from "Attachment".
- When the message is ready, click the "Send" button (preferable to just send small message without details for testing purposes as a beginner).
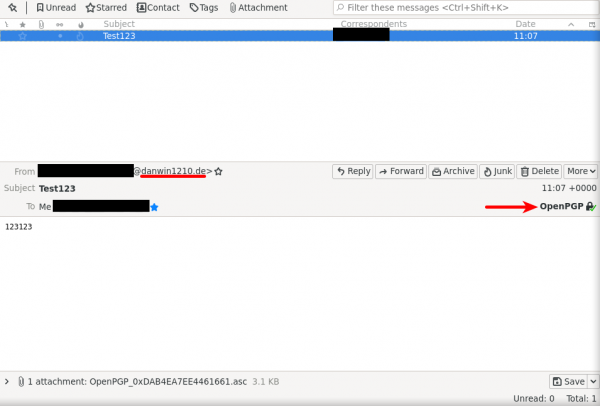
3. How the message will look like on recipient side.
- To receive new messages click "Get Messages"
- OpenPGP with green tick and padlock mean the message encrypted.
- @danwin1210.de mean the message sent over clearnet.
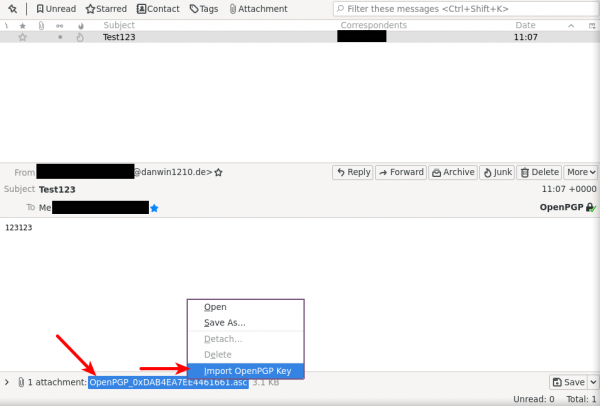
4. Recipient importing key attached by email.
- Right-Click on the attachment then choose "Import OpenPGP Key"
- Then check steps explained in Import Public Keys.
Add User ID to Key Properties
[edit]Undocumented
Export the Public Key to a GPG Server
[edit]Undocumented
Using Thunderbird with the System GnuPG Keyring
[edit]Undocumented
Final Warnings
[edit]If all steps have been successfully completed then you now have an anonymous email account paired with strong encryption.
It should be emphasized this wiki entry is not a substitute for an all-inclusive tutorial on the safest way to use GPG/PGP encryption, however it provides a solid foundation for fundamental practices. Numerous advanced resources and expert opinions exist on the Internet, and these can provide additional tips that might better address a user's perceived threat model and circumstances. [10] At a minimum, it is recommended to review the Safe Email Principles section, along with additional learning resources.
Finally, always heed the following warnings regarding email:
- Email is a very insecure means of communication where anonymity is concerned. A lot of metadata is leaked with email, so it should be used sparingly and only when strictly necessary.
- Do not contact people you know in real life at non-anonymous email addresses with the email account that was created here. Always separate real world identities from online identities used with Whonix.
- Be circumspect about sharing personal information in email! Encrypted email does not protect against the email recipient storing personal emails in an unencrypted format. Nor does encryption protect against an email recipient maliciously using personal information in order to exploit you.
- If an email is sent to a recipient without encryption, assume it can be read by anyone!
- Utilize the Tor Onion Service (.onion domain) whenever it is made available by the email provider. After first confirming the domain is controlled by the email provider, it will afford greater protection than a clearnet address.
Further Reading
[edit]Interested readers can refer to the following additional resources on GPG, GPA, and safe email practices:
Footnotes
[edit]- ↑
https://github.com/Whonix/anon-apps-config/tree/master/etc/thunderbird

- ↑ Similarly, that same information should not be stored on electronic media in the first place, if that is feasible in the circumstances.
- ↑ Installed by default in Whonix 15.
- ↑
Source:
torproject.org Gnu Privacy Guard / GnuPG
license
:
Content on this site is Copyright The Tor Project, Inc.. Reproduction of content is permitted under a Creative Commons Attribution 3.0 United States License
. All use under such license must be accompanied by a clear and prominent attribution that identifies The Tor Project, Inc. as the owner and originator of such content. The Tor Project Inc. reserves the right to change licenses and permissions at any time in its sole discretion.
- ↑ This is because packages are often unsigned, and users may forget to update the software in a timely fashion.
- ↑ https://bugzilla.mozilla.org/show_bug.cgi?id=1657901

- ↑ https://bugzilla.mozilla.org/show_bug.cgi?id=1722825

- ↑ https://thunderbird.topicbox.com/groups/e2ee/Tb249a2dc3984e8e3/getting-the-revoke-certificate

- ↑ Due to the threat of collisions, see: https://superuser.com/questions/769452/what-is-a-openpgp-gnupg-key-id

- ↑ For instance, users at high risk might generate a strong airgapped OpenPGP key pair on the command line for greater security, rather than rely on Thunderbird.

We believe security software like Whonix needs to remain open source and independent. Would you help sustain and grow the project? Learn more about our 13 year success story and maybe DONATE!