Live Mode for Kicksecure

Kicksecure can be booted in Live Mode - which forgets all user data after the session, making it ideal for sensitive data use cases. This feature is available for both Kicksecure as the host OS and Kicksecure as the guest OS.
Introduction and Definitions[edit]
A live mode offers to use an operating system (OS) without leaving any traces. If the system is started in live mode, all software can be used as normal, files can be saved, tasks can be accomplished, but after the session all data is lost and gone. This is especially important for use cases where sensitive temporary data is involved.
Kicksecure live mode can be used if Kicksecure is a guest OS or a host OS itself. A host operating system (OS) is a system that runs directly on your physical hardware. A guest OS is a system that runs inside a virtual machine. Kicksecure can be booted into live mode in both cases. We will use HOST on this page if Kicksecure is a host OS and we will use VM GUEST if Kicksecure is a guest OS inside a virtual machine.
Live mode is accomplished by use of the grub-live package![]() , a package that is developed and maintained by the developers of Kicksecure and Whonix. grub-live can also be used by other Linux distributions because it is Freedom Software.
, a package that is developed and maintained by the developers of Kicksecure and Whonix. grub-live can also be used by other Linux distributions because it is Freedom Software.
NOTE: This is unfortunately not available in Kicksecure for Qubes, but available in all other Kicksecure variants.
What data will be forgotten?[edit]
Booting into live mode will ensure all disk writes to the virtual hard drive are forgotten after shutdown because all writes go to volatile memory (RAM) instead of the hard disk. In other words, after shutdown everything that happened during a previous boot session will not be visible (persist) on the virtual hard drive, including:
- everything that is created / changed / downloaded
- any websites visited, files downloaded or documents created; and
- any other modifications of the virtual hard drive or activity history.
- This also holds true for malicious changes made by malware. For Kicksecure as VM GUEST also read our chapter #Helpful_tips_against_attack_vectors regarding malware.
Getting Started[edit]
Preparation[edit]
Applicability: These instructions are only necessary for users intending to use live mode. Users who always (or mostly) use persistent mode (the default boot option) can disregard these instructions.
For the very first time Kicksecure is started, please start it in persistent mode (the option is simply named "Kicksecure"), NOT in live mode. This will allow Tor to make use of Tor Entry Guards for automatic initial setup.
From the second time Kicksecure is started onwards, the user may opt-in to run it in live mode if non-persistence, amnesia is desired.
Starting Live Mode[edit]
- Kicksecure: No special notice.
- Kicksecure-Qubes: Unavailable. [1]
If you're Kicksecure VM is already running (VM GUEST) shut it down first then power on the VM again to get into the boot menu. If your running Kicksecure as HOST simply restart your machine.
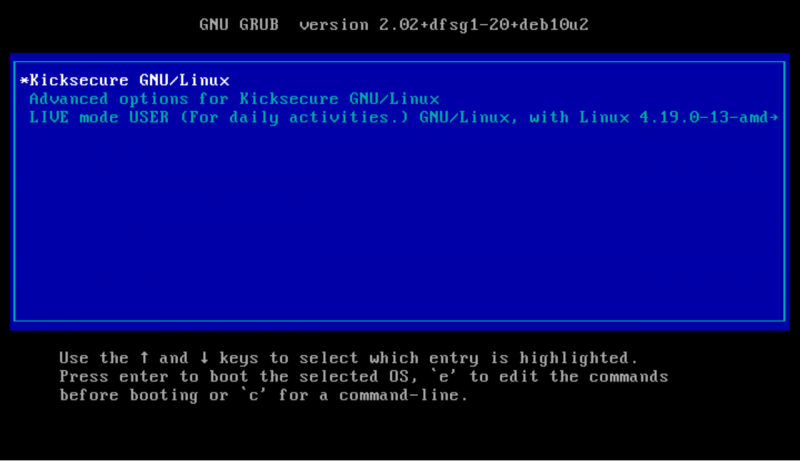
During the grub boot menu (read more about grub bootloader here) wait until you see the following. Consider: There are 3 options, the selected option is indicated by the asterisk symbol ![]() . Read those options to understand their basic meaning. Below persistent mode is selected. Persistent mode is the "normal" mode.
. Read those options to understand their basic meaning. Below persistent mode is selected. Persistent mode is the "normal" mode.
Figure: Persistent Mode Boot
In total you have 3 options

Kicksecure GNU/LinuxAdvanced options for Kicksecure GNU/LinuxLIVE mode USER (For daily activities.) GNU/Linux ...
What is currently selected? The asterisk symbol ![]() indicates the currently selected boot option. The white text color on the blue background also indicates the currently selected boot option.
indicates the currently selected boot option. The white text color on the blue background also indicates the currently selected boot option.
Can I choose multiple options at once? You can only select one option at a time. Other currently unselected boot options have light blue text color and NO asterisk at the front.
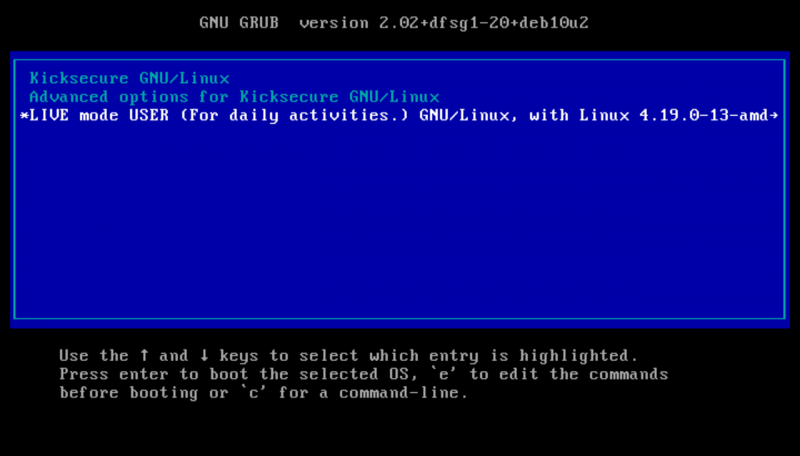
Use the arrow keys (up ↑ and down ↓) on the keyboard to switch to the option LIVE mode USER (For daily activities.).
Figure: Live Mode Boot (non-persistent)
After you've selected live mode simply press enter.
The system is now booting into live mode.
Functionality Test of Live mode[edit]
If you want to independently verify if live mode is working, follow these steps.
1. Run live mode (see #Starting Live Mode).
2. Create a new file in your /home/user directory.
Could be any file such as for example a small text file.
3. Reboot your machine (HOST). Or restart (via virtualizer) or reboot your Kicksecure VM (both VM GUEST).
4. After then reboot is complete check if you can find that file. If it's gone then live mode is functional.
5. Done.
The live mode functionality test has been completed.
HOST specifics (Kicksecure as host OS)[edit]
Best practices[edit]
It is recommended to use Live mode as a standard for sensitive data use cases. Live mode is also a useful tool for better privacy on the hard drive, as well as experimental changes like testing software.
But it is also recommended regularly boot into persistent mode (for example once per day) for installation of updates.
Live mode undefeated, even by persistent malware[edit]
For some users persistent malware is a concern. A persistent malware compromise after reboot however would require targeted malware which gains super user (root) access to re-mount the disk for write access. But re-mounting the disk for write access is not yet a default feature available to off-the-shelf malware; no such reports have come to our attention.
Boot standard - live mode or persistent mode[edit]
There are two choices:
grub-live(grub-live instructions here): Boots into persistent mode by default. The grub boot menu has an option to boot into live mode.grub-default-live(grub-default-live instructions here): Boots into live mode by default. The grub boot menu has an option to boot into persistent mode.
Kicksecure live mode vs Tails comparison[edit]
Kicksecure live mode is based on the grub-live package which is developed and maintained by the team behind Kicksecure and Whonix. The grub-live package is not only available for Whonix and Kicksecure, but also for many other Linux distributions. To compare Tails and Kicksecure live mode, see grub-live#comparison_between_grub-live_and_Tails.
VM GUEST specifics (Virtual Machine VM)[edit]
VM Live mode and RAM[edit]
Anti-Forensics[edit]
VM Live Mode is NOT an anti-forensics feature! This is due to the limitations of the virtual machine. For anti-forensics check out Live Mode as HOST, described above.
Helpful tips against attack vectors[edit]
To keep your live mode unaffected even by malware memorize these instructions and follow them regularly.
Table: VM Live Mode Warnings
| Domain | Recommendations |
|---|---|
| Forensics | By itself, starting a VM in live mode is not amnesic. Many users are unaware that activities performed inside the VM might be stored on the host mass storage device (hard drive, HDD, SSD) in locations that are hard to review (for the majority). Extra steps must be performed on the host operating system to minimize these traces -- see Anti-Forensics Precautions, or better, use Live Mode as HOST. |
| Malware | To prevent malware from remounting the hard drive as read-write it is strongly recommended to use read-only hard drive mode. This raises the bar as malware would need to break out of the VM to gain persistence, because there might be data leaks if
|
| Other Precautions |
|
VM Live Mode vs VM Snapshots[edit]
Readers of this chapter should already be familiar with Kicksecure live mode, as described in the other chapters on this page, as well as the concept of VM snapshots.
Starting with a clean VM snapshot and later reverting to that snapshot should be even safer than using VM live mode. This is because snapshots are enforced from outside the VM, by the virtualizer. Therefore, snapshots are more secure.
It is also worth noting that running VM live mode uses more RAM than is allocated to the guest, since the OS runs entirely in memory. This means that, in some cases, it is more likely for VM live mode to experience disk thrashing![]() , where the VM uses up all the allocated memory and becomes significantly slower. The snapshot approach does not have this issue with RAM.
, where the VM uses up all the allocated memory and becomes significantly slower. The snapshot approach does not have this issue with RAM.
It is difficult to imagine a case currently where the combination of VM live mode with reverting to a clean snapshot would be even safer. Perhaps in the case of a virtualizer bug with snapshots and/or user error forgetting to revert to a snapshot.
For even greater security, the user could consider Live Mode HOST or even host disk snapshots, such as Raw Disk Backup, although this would unfortunately be more cumbersome and time-intensive.
Troubleshooting[edit]
For known issues, see Live Check Systray Issues.
Host Live Mode in Combination with VM Live Mode[edit]
If the host operating system is booted in live mode, that includes everything that is running on the host. This means it also includes any VMs running on the host.
Therefore it is unnecessary to run VMs in live mode if the host is already running in live mode. The VMs will report that they are not running in live mode but they don't know any better and have no way to know by design.
The user could perform a Functionality Test of Live mode to verify this.
See Also[edit]
Forum Discussion about live mode[edit]
See: Whonix live mode / amnesia / amnesic / non-persistent / anti-forensics![]()
Footnotes[edit]
- ↑
Qubes issue: implement live boot by porting grub-live to Qubes - amnesia / non-persistent boot / anti-forensics

- ↑ There are two live mode options available,
grub-live and
and ro-mode-init .
.
grub-live: a new boot menu entry is created which must be selected manually, but it is a better failsafe and hence the recommended option.ro-mode-init: the boot menu stays the same and the system automatically boots into live mode when it detects a read-only disk, otherwise it boots normally into persistent mode. The advantage of using this approach is that malware running in a VM cannot silently change settings to leave persistent traces.
Unfinished: This wiki is a work in progress. Please do not report broken links until this notice is removed, use Search Engines First and contribute improving this wiki.

We believe security software like Kicksecure needs to remain Open Source and independent. Would you help sustain and grow the project? Learn more about our 12 year success story and maybe DONATE!