Build Documentation: Physical Isolation

Security by Isolation. Using Whonix with Physical Isolation on Bare Metal for Better Security.
Introduction
[edit]Overview
[edit]Physical isolation requires:
- A supported platform that can run Whonix. There are also others.
- Also refer to Physical Isolation Security and Support Status.
First Time Users
[edit]
Technical Introduction
[edit]The default Whonix configuration consists of two virtual machines (VMs) running on the same physical host. This means any exploits targeting the VM implementation or the host can still break out of the torified client VM and expose the IP address of a user. Further, any malware running on the host has full control over all VMs. To protect against these attacks a different approach is required -- physical isolation. In this configuration the gateway system is installed on separate hardware, which drastically reduces the trusted computing base (TCB)![]()
by more than half.
The following instructions describe how to install and configure two computers and set up an isolated point to point network between them. [2] This way one computer acts as the client (Whonix-Workstation™), while the other is the proxy (Whonix-Gateway™) which transparently routes all the Whonix-Workstation™ traffic via Tor.
The Whonix-Gateway on its own physical device can be run either directly on hardware or inside a VM. Both options have distinct advantages and disadvantages, but using an additional VM for the Whonix-Gateway is unrecommended. In contrast, the Whonix-Workstation should always be installed in a VM because this will hide hardware serial numbers. Also read the wiki entry recommending use of multiple VM Snapshots for better security.
In this configuration the host operating system(s) should only be used for downloading operating system updates, hosting Whonix-Gateway or Whonix-Workstation and nothing else. The configuration is also more secure if the physical systems are exclusively used for hosting Whonix, or if storage devices are separated for Whonix and non-Whonix use cases. The reason is this avoids any potential infection of the Whonix hard drive by another operating system.
Warnings
[edit]Please note the following warnings about physical isolation:
- This configuration is less tested than VM builds. More rigorous testing by the Whonix community is required.
- These instructions are difficult to comprehend for non-technical Linux users.
- Build Anonymity has not been considered for this wiki chapter. [3]
- It is essential to read the warnings in the latest build instructions for VM images. Some of these apply to physical isolation such as Don't add private files to Whonix source code folder! and Check if the OpenPGP public keys are still up to date.
- This chapter currently lacks detail concerning Whonix-Gateway and Whonix-Workstation MAC addresses, see:
- Joanna Rutkowska

, security researcher, founder and developer emeritus of Qubes OS

has completed a research paper comparing the security of software compartmentalization vs. physically separated computers

(pdf). It concluded that in some cases, notably for specific, desktop-related workflows, Physical Isolation might be less secure than Qubes' compartmentalized approach. (See also: Qubes-Whonix.)
Configuration
[edit]Physical Isolation Configuration
[edit]| Configuration | Advantages | Disadvantages |
|---|---|---|
| Spare Hardware and VM |
|
|
| Spare Hardware without VM |
|
|
Hardware Configuration
[edit]It is recommended that two dedicated computers are utilized for Whonix that are never used for activities that could reveal your identity. Alternatively, an existing computer that is already in use can be utilized for Whonix-Gateway. To offer some isolation, all internal and external drives should be disconnected, with boots occuring from an eSATA, USB or another internal drive into a clean environment.
For non-anonymous use, the physical arrangement can be used as is without any modification. This includes the use of a non-anonymous home (dial-up) Internet router, without any changes. In contrast anonymous use requires:
- Whonix-Gateway
- an anonymous 3G/4G/5G modem or an anonymous WiFi adapter (see below)
- Whonix-Workstation
In terms of the specific hardware used for Whonix-Gateway, various devices are feasible and it does not have to be a big desktop computer or ordinary server. Alternatives include:
- smartphone [4]
- ultra-mobile personal computer (UMPC)

- pad or tablet
- notebook or netbook
- formerly a Raspberry Pi

[5]
- router [6]
- set-top box

- and other suitable devices
How to utilize devices like a Linux server is beyond the scope of this chapter and better resources already exist on the Internet. Similarly for Whonix-Workstation, a device that is suitable should be chosen.
Pre-installation Prerequisites
[edit]Prerequisites
[edit]Physical isolation has several prerequisites:
- System requirements: Available hardware must meet the minimum specifications.
- Whonix-Gateway: A device with at least two network adapters -- at least one of them ethernet [7] -- capable of running Linux. The Whonix-Gateway will run Debian. [8]
- Whonix-Workstation: A device connected via ethernet to the Whonix-Gateway. It must only have this one NIC and no other network connectivity! It must also be connected by wire. [9] This will be the torified client system or Whonix-Workstation and it must be capable of running Debian. [10]
- VM client: It is recommended to use a VM as the client, namely the same Whonix-Workstation that most "normal" (non-physical isolation) Whonix users rely upon. [11] [12] [13]
- Host build environment: The build environment must have a working Internet connection to Debian mirrors.
- Virtual console: Although optional, it is also useful to know how to open a second virtual console.
Host Preparation
[edit]1. Prepare to build on Debian trixie.
To obtain Debian safely, see: Debian ISO OpenPGP verification. Around 15 GB of free space is required. [14]
2. Adjust terminal settings.
It is recommended to set the terminal (such as Konsole) to unlimited scrollback, so it is possible to watch the full build log.
3. Install build dependencies.
Install build dependencies and get the source code.
Update the package lists.
sudo apt update
Install build dependencies.
sudo apt install git time curl approx lsb-release fakeroot dpkg-dev fasttrack-archive-keyring safe-rm
System Preparation
[edit]1. Confirm prerequisites are met.
- Debian
trixieis installed. - User account
userexists.
su -
3. Install sudo and adduser packages.
1. Update the package lists.
apt update
2. Upgrade the system.
apt full-upgrade
3. Install sudo and adduser packages.
apt install --no-install-recommends sudo adduser
4. Set user rights.
The following commands must be run either by root or using sudo.
Create group console.
addgroup --system console
Add user user to group console.
adduser user console
Add user user to group sudo.
adduser user sudo
5. Reboot. [17]
reboot
How-to: Install Whonix-Gateway
[edit]Recommended: On Hardware
[edit]Get Debian
[edit]Download a Debian trixie 64-bit installation ISO![]()
. Detailed instructions for this procedure are not part of this chapter, but the Debian Host Operating System Tips chapter provides some steps.
It is possible to choose an ISO for any desktop environment (LXQt, GNOME, KDE, LXDE, ...). However, because the command line is extensively used the Debian trixie network install (netinst) version is recommended (it is the most minimal).
Install Debian
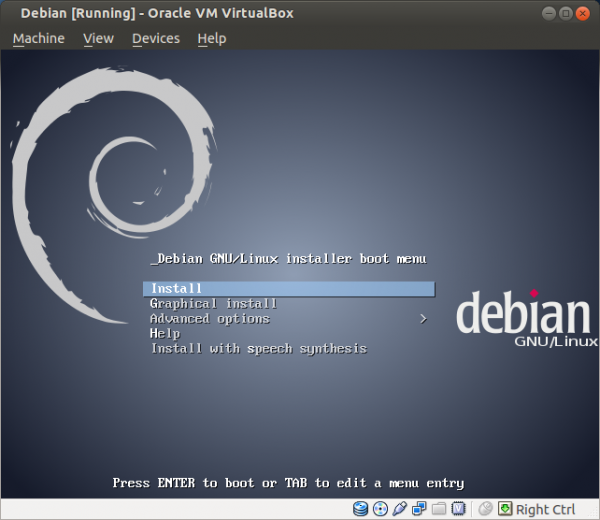
[edit]In the installer boot menu of Debian trixie, press "Install" and choose the following settings:
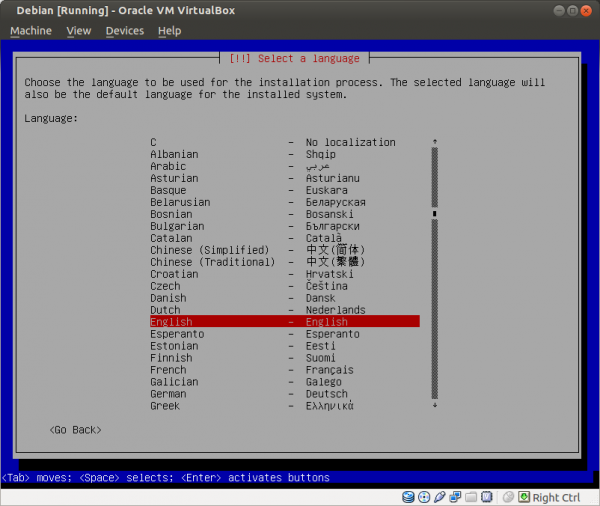
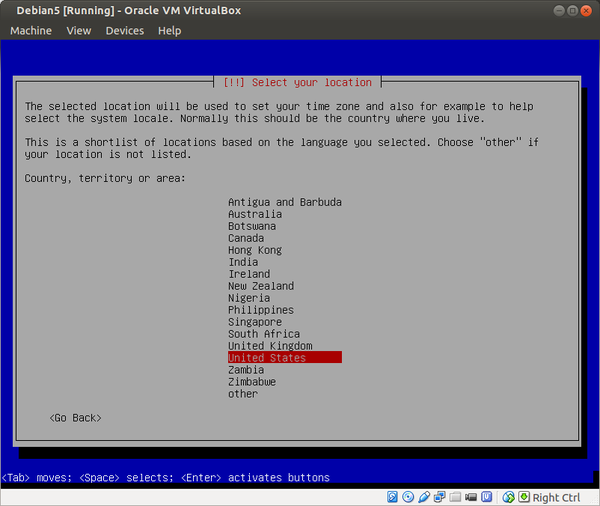
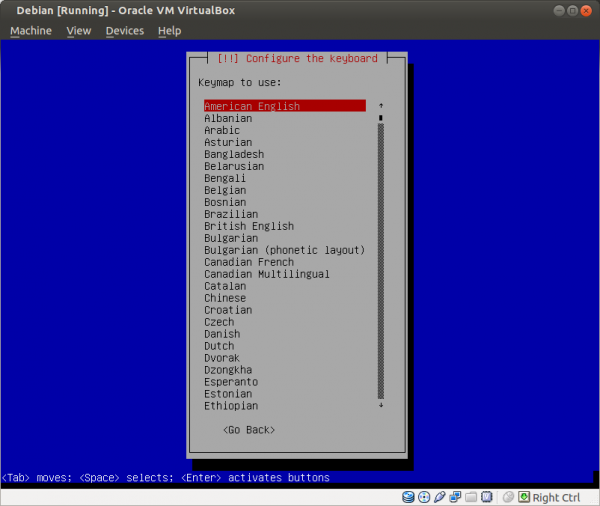
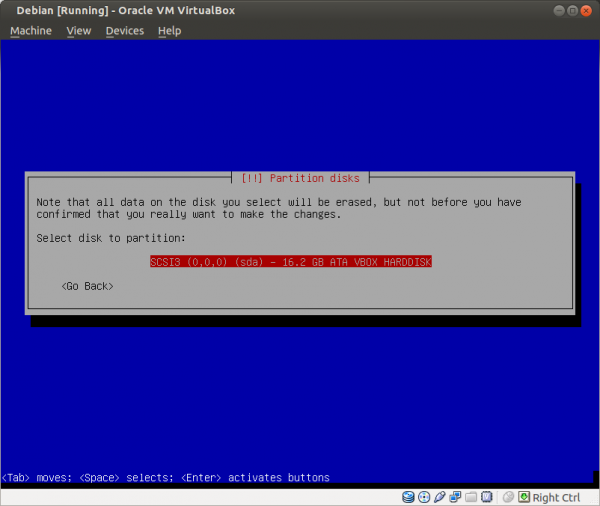
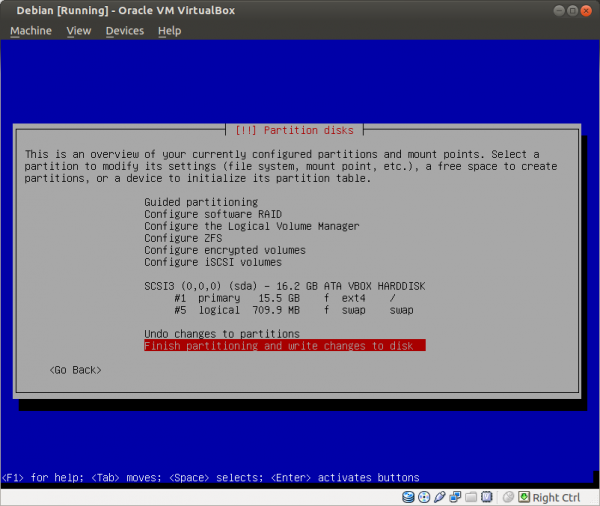
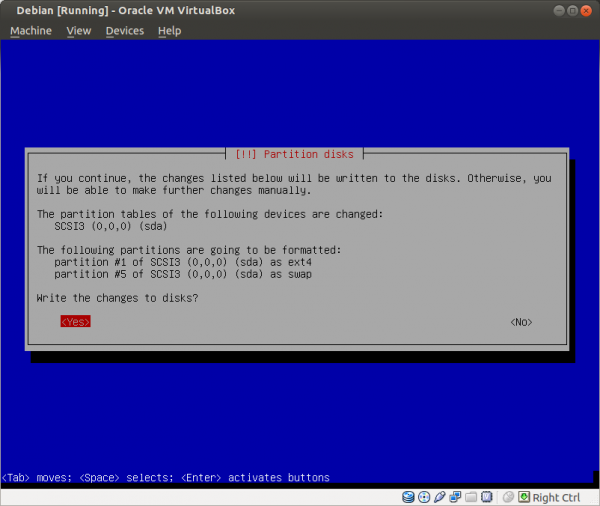
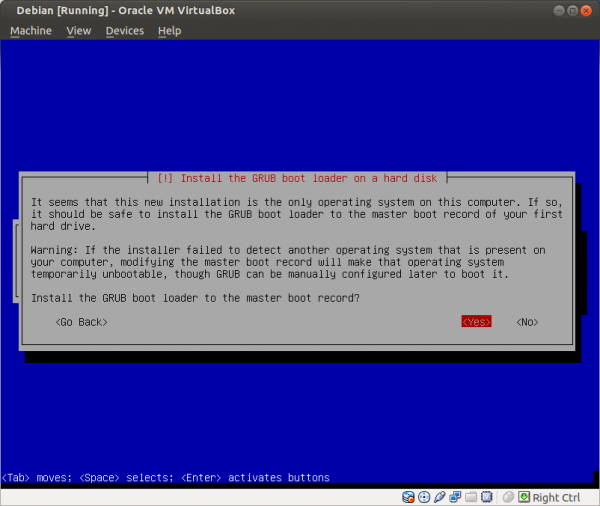
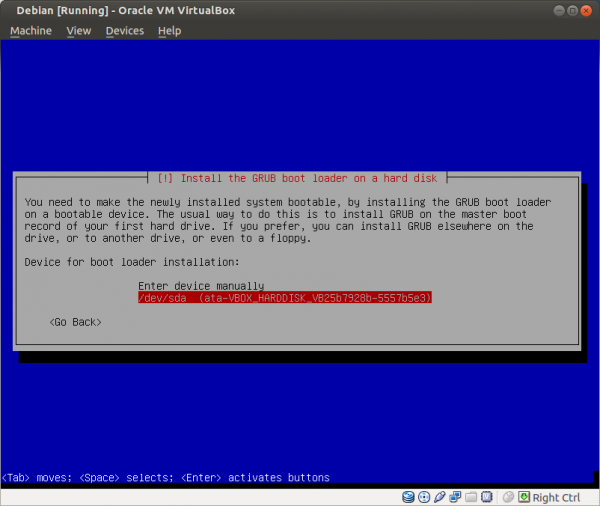
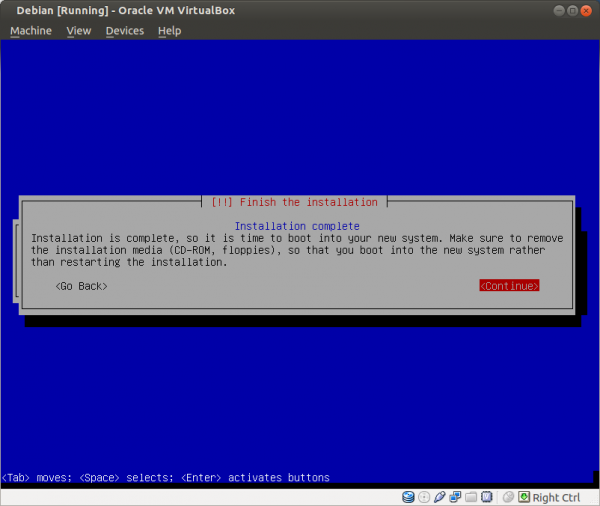
Select a language: English Select your location: United States Configure the keyboard: (select yours) Hostname: host Domain name: (empty) Root password: (set up a strong password) Full name for the new user: user Username for your account: user Password for the new user: (choose a good password, different from root password) Partitioning method: Guided - use entire disk (it is a good idea to set up cryptsetup encrypted LVM at this point) Partitioning scheme: All files in one partition (select the listed device in the next step) Partition disks/overview: Finish partitioning Write changes to disk: Yes Debian archive mirror country: Go back Continue without a network mirror: Yes Use a network mirror: No Participate in the package usage survey: No Software selection: None; deselect all options (using Space) Install the GRUB boot loader: Yes (select the listed device in the next step) Finish the installation: Continue
Installation Screenshots
[edit]For a visual walk-through of the minimal Debian trixie installation, click on Expand on the right. For up-to-date screenshots of this process, refer to the The Debian Administrator's Handbook: 4.2. Installing, Step by Step![]()
. If utilizing this guide, remember to set:
- the English language
- the United States location
- hostname to "host"
- an empty domain name
- a strong root password
- full name to "user"
- username to "user"
- a strong user password
- full disk encryption (recommended)
- installation without a mirror
- refuse survey participation
Figure: Select "Install"
Figure: Set English Language
Figure: Set United States Location
Figure: Keyboard Selection
Figure: Additional Content Installation
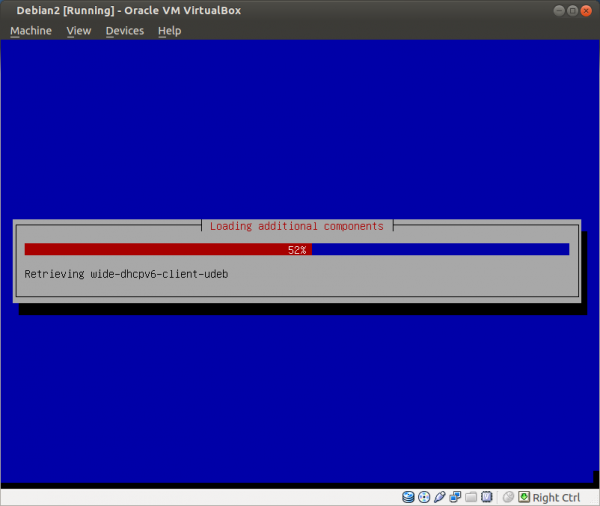
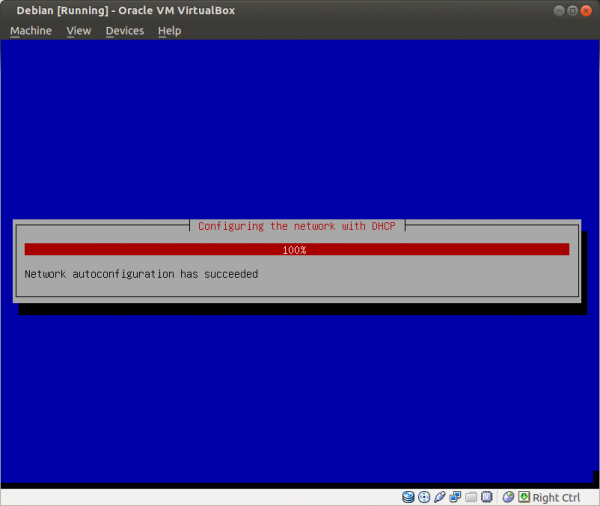
Figure: Network Auto-configuration [18]
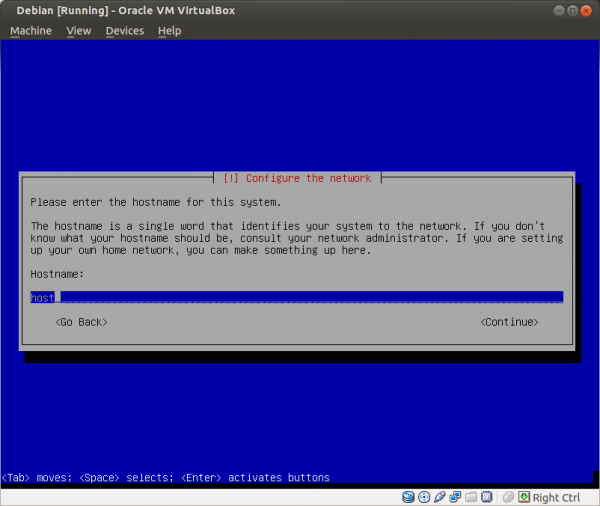
Figure: Set Hostname to "host"
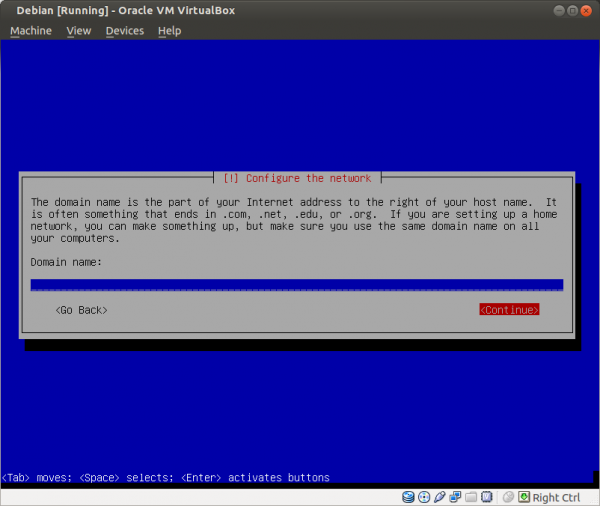
Figure: Set Empty Domain Name
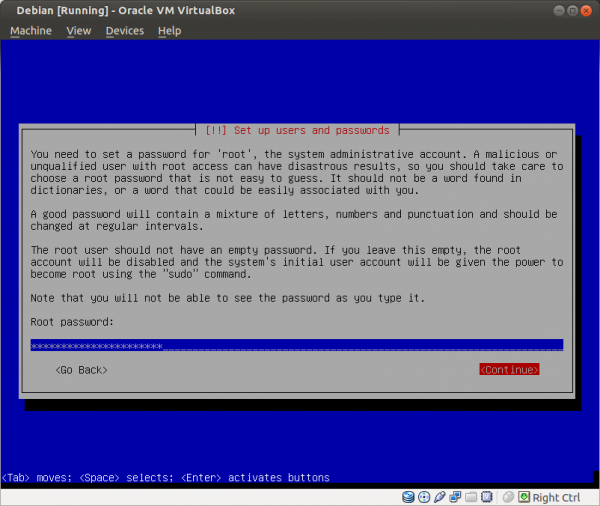
Figure: Enter a Strong Root Password
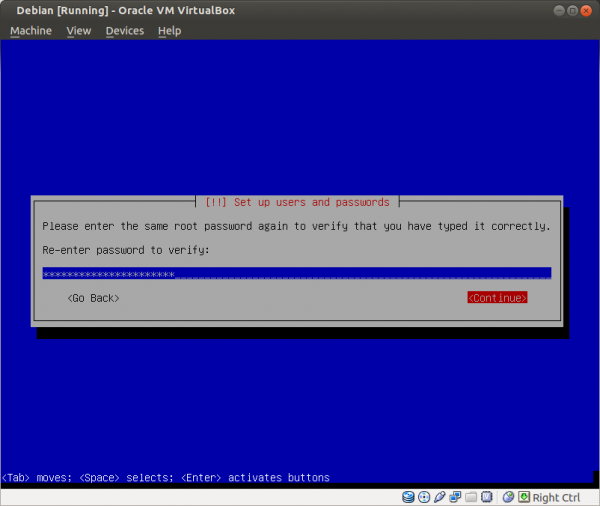
Figure: Re-enter the Password
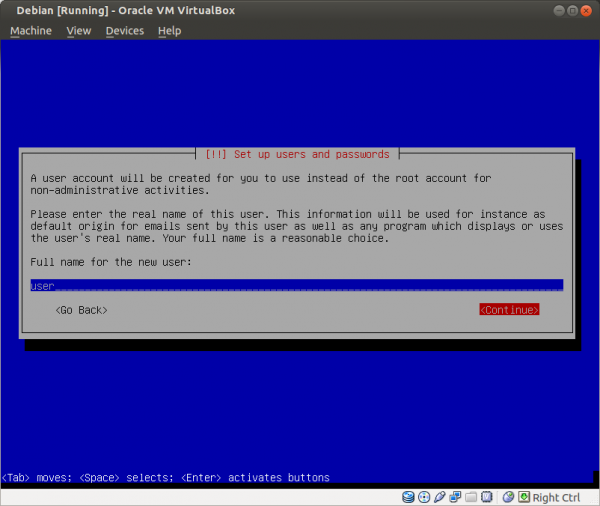
Figure: Set Full Name to "user"
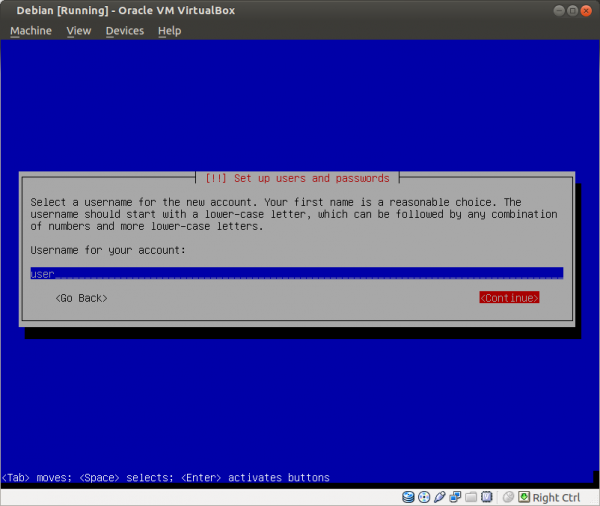
Figure: Set Username to "user"
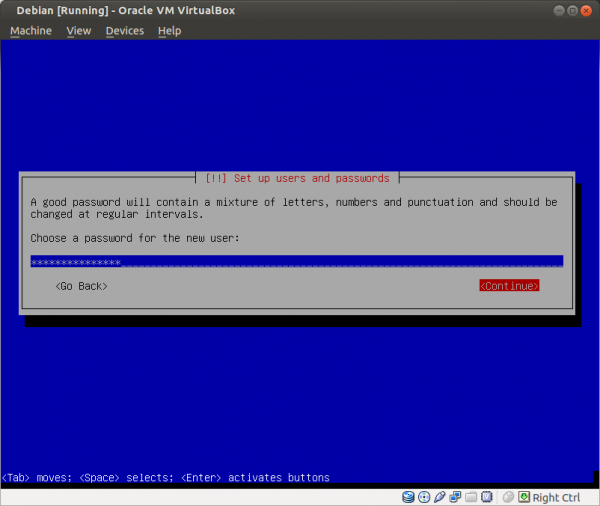
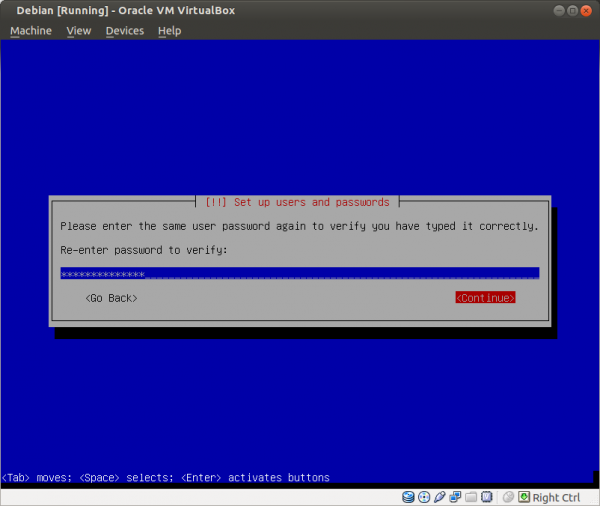
Figure: Enter a Strong user Password
Figure: Re-enter the Password
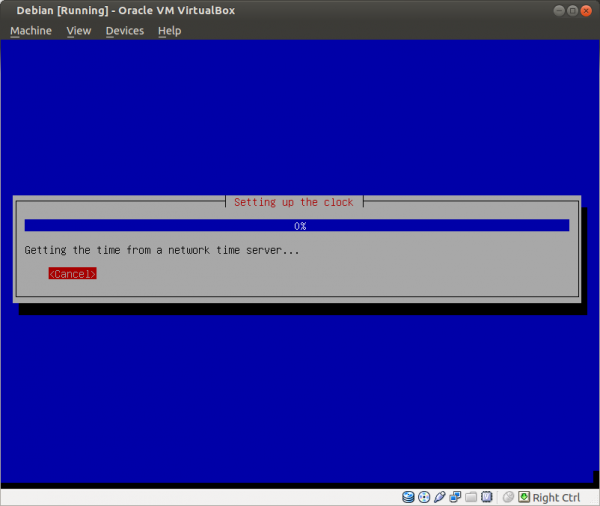
Figure: Network Time Procedure
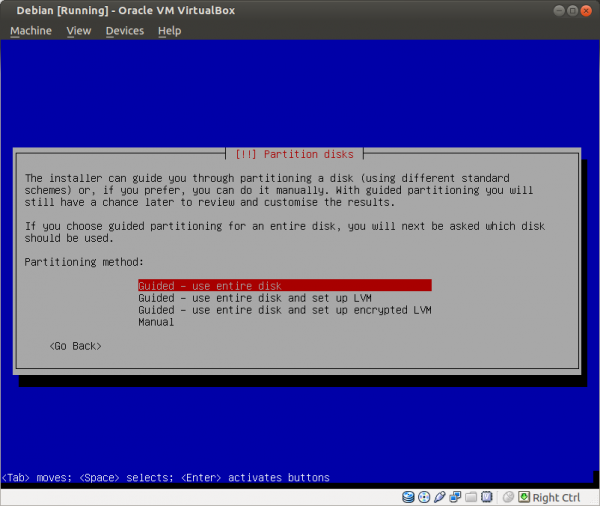
Figure: Use a Guided Partitioning Method with the Whole Disk [19]
Figure: Select the Suggested Disk
Figure: Partition all Files in One Partition
Figure: Finish Partitioning
Figure: Confirm Changes
Figure: Wait for Base System Installation [20]
Figure: Do not Select a Mirror [21]
Figure: Confirm Continuation without a Mirror
Figure: APT Configuration
Figure: Refuse Survey Participation [22]
Figure: Deselect (no star) the Given Option [23]
Figure: Install GRUB
Figure: Select the Disk
Figure: Finish Installation
Figure: Automatic System Reboot
Figure: Operating System Screen
Figure: Login Screen
Optional: Customizing Full Disk Encryption
[edit]If you wish to configure a custom encryption algorithm to enhance security during the minimal Debian trixie installation, click on Expand on the right.
1. Under "Partitioning method", select Manual.
2. Select the installation disk.
Highlight the installation disk and press "Enter"→Select <Yes> to create a new empty partition table
3. Create a new partition.
Select the "FREE SPACE" of the destination drive you are installing to→Press "Enter"→"Create a new partition" should already be selected→Press "Enter" again
4. Create a boot partition.
This is the unencrypted partition the system boots from; the standard size is 254.8 MB.
Type "254.8 MB" (without the quotes)→Press "Enter"
5. Select partition type and location.
Check "Type for the new partition:" -- "Primary" should already be selected→Press "Enter"→Under "Location for the new partition:" -- "Beginning" should already be selected→Press "Enter"→Navigate to the Partition settings screen
Use the following settings for the boot partition:
Use as: Ext4 file system Mount point: /boot Mount options: noatime Label: none Reserved blocks: 5% Typical Usage: standard Bootable flag: on
Next, select "Done setting up the partition" and press Enter. You will be brought back to the main partitioning menu.
6. Select encrypted volumes option.
Choose "Configure encrypted volumes"→Press "Enter"→Select <Yes> when asked to write the changes to disk and configure encrypted volumes
7. Configure the encrypted partition.
Ensure "Create encrypted volumes" is already selected→Press "Enter"→Select the free space of the installation drive by pressing the spacebar→Select <Continue> and press "Enter" again
After additional components load, a configuration page for the encrypted partition will appear. At this stage it is possible to customize the encryption settings.
Use as: physical volume for encryption Encryption method: Device-mapper (dm-crypt) Encryption: twofish [Recommend "twofish" and "serpent" as alternatives. "Serpent" is the slowest and only recommended if you have a fast system (and a fast drive), as it creates a lot of system overhead. "Twofish" is an algorithm created by Bruce Schneier, and is a lot faster, computationally-speaking. For most use-cases, "twofish" should be sufficient as an alternative algorithm] Key size: 256 (leave as-is) IV algorithm: xts-plain64 [for most use-cases, xts-plain64 should be sufficient. Do not change this unless you know what you are doing. You could inadvertently create a security hole] Encryption key: Passphrase (leave as-is) Erase data: yes (this will wipe the partition) Bootable flag: off
8. Write the changes to disk.
After completing the configuration step:
Select "Done setting up this partition"→Press "Enter"→Select <Yes> and press Enter to write the changes to disk→On the next screen select "Finish" and press "Enter"
9. Optional: Erase the partition.
It is strongly recommended to erase the partition before continuing. Please note this may take a while for large drives. If the device was securely wiped before starting this installation, this step can be skipped. To erase the partition, select <Yes> and press Enter.
10. Choose a strong password.
Refer to this entry for advice on generating strong passwords with sufficient entropy; at least a 7-word diceware passphrase is recommended. [24] [25] Remember: the stronger the passphrase, the stronger your encryption (and vice-versa). After entering the passphrase and confirming it, you will be brought back to the main partitioning menu.
11. Configure the physical volume.
Inspect the new "Encrypted volume" (which should be at the top of the list)→Highlight the partition that was just created under it (it should say ext4)→Press "Enter"→Under "Use as:" -- change this to "physical volume for LVM"→Press "Enter"→Select "Done setting up the partition"→Press "Enter" again to be brought back to the main partitioning menu
12. Select "Configure the Logical Volume Manager" and press Enter.
13. Configure the volume group.
Highlight "Create volume group" and press "Enter"→Under "Volume group name:" -- enter HOST_VG and press "Enter
14. Use the spacebar to select the encrypted partition, then select <Continue> and press Enter.
(Optional) SWAP USERS: O1. Now create your swap partition. Highlight "Create logical volume" and press Enter, then select HOST_VG and press Enter again. Type SWAP, press Enter. O2. Enter your volume size (2.5 GB is usually a good standard size for most systems) then select <Continue> and press Enter.
15. Create the logical volume.
Highlight "Create logical volume" → Press "Enter" → Select HOST_VG → Press "Enter" → Type ROOT → Press "Enter"
16. Under the "Logical volume size:", the entire volume should already be displayed. Press Enter again.
17. Highlight "Finish", then press Enter to be brought back to the main partitioning menu.
18. The new partition for ROOT should be displayed on this screen [LVM VG HOST_VG, LV ROOT - xxx.x GB Linux device-mapper (linear)]. Select the partition underneath the heading and press Enter.
19. Select the preferred filing system.
Change "do not use" to the filing system of your choice; ext4 is good for most installations, while XFS is more suitable for filesystems on top of encryption and is more robust with better performance. For the purpose of this chapter, the following configuration is provided:
Use as: XFS journaling file system Mount point: / Mount options: defaults Label: none
20. When the preceding configuration is finished, select "Done setting up this partition" and press Enter to return to the main partitioning menu.
(Optional) SWAP USERS: O1. You should see your new partition for SWAP displayed on this screen [LVM VG HOST_VG, LV SWAP - 2.5 GB Linux device-mapper (linear)]. Select the partition underneath the heading and press Enter. O2. Change "do not use" to "swap area", and press Enter. Then select "Done setting up the partition" to return to the main partitioning menu.
21. Finalize the partitioning.
Highlight "Finish partitioning and write changes to disk"→Press "Enter"→Select <Yes> when asked to confirm the changes
The installation will continue automatically.
Network Configuration
[edit]The external interface (usually eth0) may need to be configured according to the requirements of your local network, for example static or simply left to use DHCP if the gateway is connected to a DHCP-capable router. For wlan, refer to upstream wiki documentation:
Check that the Internet is working.
Log On and Upgrade Debian
[edit]1. Install security updates.
Log on, install all security updates and reboot.
2. Log in with "root".
3. Add the trixie main contrib non-free repository source.
echo "deb https://deb.debian.org/debian trixie main contrib non-free" >> /etc/apt/sources.list
4. Add the trixie updates repository source. [26]
echo "deb https://security.debian.org/debian-security trixie-security main" >> /etc/apt/sources.list
5. Refresh package lists and upgrade.
apt update && apt full-upgrade -y
Firmware Updating and Security Problems
[edit]Processor microcode updates are recommended to address speculative execution flaws; see Firmware Updating and Security Problems for further information.
Update the package lists.
sudo apt update
For Intel.
sudo apt install --no-install-recommends iucode-tool intel-microcode
For AMD.
sudo apt install --no-install-recommends amd64-microcode
Preparation
[edit]1. Install sudo and git. [27]
## Install "sudo" and git. apt install sudo git -y
2. Prepare the system for the Whonix build.
You must build as user "user" and that user must be a member of the "sudo" group. Rebooting applies the changes.
## Add "user" to "sudo" group adduser user sudo ## Reboot the system shutdown -r now ## (host) login with "user" user
3. Optional: Consider taking an image of the installation in case the build script fails partway through.
Get the Source Code
[edit]Get the Signing Key
[edit]Get the Whonix Signing Key and import it.
Get the Source Code
[edit]1 Install git.
sudo apt update && sudo apt install git
2 Get the source code including git submodules. [28] [29]
Note: Replace 18.1.4.2-developers-only with the actual tag or branch you intend to build.
git clone --depth=1 --branch 18.1.4.2-developers-only --jobs=4 --recurse-submodules --shallow-submodules git@github.com:Whonix/derivative-maker.git
3 Check if the above command succeeded.
If there were errors such as:
fatal: unable to access 'https://github.com/.../': Could not resolve host: github.com
Or:
fatal: unable to access 'https://github.com/.../': gnutls_handshake() failed: The TLS connection was non-properly terminated.
then the download likely failed.
Verify success by checking the exit code.
Choose your shell.
4 Done.
Git repository cloning has been completed.
OpenPGP Verify the Source Code
[edit]This chapter is recommended for better security, but is not strictly required. (See Trust.)
- Digital signatures are a tool enhancing download security. They are commonly used across the internet and nothing special to worry about.
- Optional, not required: Digital signatures are optional and not mandatory for using Whonix, but an extra security measure for advanced users. If you've never used them before, it might be overwhelming to look into them at this stage. Just ignore them for now.
- Learn more: Curious? If you are interested in becoming more familiar with advanced computer security concepts, you can learn more about digital signatures here: Verifying Software Signatures
1. Verify the chosen tag to build.
Note: Replace with the tag you want to build.
git verify-tag 18.1.4.2-stable
2. Check the output of the verification step.
If the file is verified successfully, the output will include Good signature, which is the most important thing to check.
gpg: Good signature
This output might be followed by a warning as follows.
gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner.
This message does not alter the validity of the signature related to the downloaded key. Rather, this warning refers to the level of trust placed in the Whonix signing key and the web of trust. To remove this warning, the Whonix signing key must be personally signed with your own key.
2. Verify the git commit to build. [32]
Note: Replace 18.1.4.2 with the actual git tag being verified.
git verify-commit 18.1.4.2-stable^{commit}
3. Check the output of the verification step.
4. Done.
Choose Version
[edit]1 Retrieve a list of available git tags.
git --no-pager tag
2 Use git checkout to select the preferred version to build.
Note: Replace 18.1.4.2-stable with the actual version chosen for the build. Common sense is required when choosing the right version number. For example, the latest available version number is not necessarily the most stable or suitable. Follow the Whonix News Blog as it might contain information.
git checkout --recurse-submodules 18.1.4.2-stable
3 Digital signature verification.
Optional. If you choose to perform digital signature verification above, you can verify the currently chosen commit (HEAD) again for additional assurance.
git verify-commit HEAD
4 Done.
Version selection has been completed.
Check Git
[edit]1. Check if you really got the version you want.
git describe
The output should show.
18.1.4.2-stable
2. Check if source folder is pristine.
git status
Output should be the following.
- A)
HEAD detached at 18.1.4.2-stable
nothing to commit, working tree clean
or,
- B)
Not currently on any branch. nothing to commit, working tree clean
If it shows something else, do not continue.
3. Done.
Optional Build Configuration
[edit]Refer to Optional Build Configuration for additional configuration options like:
- 32-bit vs 64-bit builds
- Whonix APT repository
- APT onion build sources
- torified or host APT cache
- build variables changes
- skipping steps
- source code changes
Network Verification
[edit]Before running the derivative-maker script make sure eth0 and eth1 refer to the correct interfaces.
## May be helpful. dmesg | grep eth
If non-default network interface names are in use, please click on Expand on the right.
One method is figuring out how to change a network interface name such as wlan0 to eth0.
Another method is to consider changing the network interface names in the configuration files. To discover components that require configuration changes in the Whonix source folder, the following commands may be helpful. Note that only a few files should require modification and the variables eth0 and eth1 have been used wherever possible.
exclude="--exclude=README.md --exclude=control --exclude=changelog.upstream --exclude-dir=.git --exclude-dir=developer-meta-files --exclude-dir=build-steps.d --exclude-dir=qubes-whonix"
grep $exclude -r eth0 ~/derivative-maker grep $exclude -r eth1 ~/derivative-maker
grep -l $exclude -r eth0 ~/derivative-maker grep -l $exclude -r eth1 ~/derivative-maker
If you decide to edit these files in Whonix source folder, remember to apply the build parameters from the Source Code Changes section here.
The final and perhaps best method is changing the network interface names after the Whonix build script has finished; see below.
1. Note the location for network interfaces.
For example /home/user/Whonix/packages/whonix-ws-network-conf/etc/network/interfaces.d/30_non-qubes-whonix becomes /etc/network/interfaces.d/30_non-qubes-whonix.
2. Create a firewall drop-in configuration snippet.
- Do not edit
/usr/bin/whonix_firewall. - Instead, create a drop-in config snippet here:
/etc/whonix_firewall.d/30_default.conf.
Open file /etc/whonix_firewall.d/50_user.conf in an editor with administrative ("root") rights.
1 Select your platform.
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand.
3 Open the file with root rights.
sudoedit /etc/whonix_firewall.d/50_user.conf
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand. - Template requirement: When using Qubes-Whonix, this must be done inside the Template.
3 Open the file with root rights.
sudoedit /etc/whonix_firewall.d/50_user.conf
4 Notes.
- Shut down Template: After applying this change, shut down the Template.
- Restart App Qubes: All App Qubes based on the Template need to be restarted if they were already running.
- Qubes persistence: See also Qubes Persistence

- General procedure: This is a general procedure required for Qubes and is unspecific to Qubes-Whonix.
2 Notes.
- Example only: This is just an example. Other tools could achieve the same goal.
- Troubleshooting and alternatives: If this example does not work for you, or if you are not using Whonix, please refer to Open File with Root Rights.
3 Open the file with root rights.
sudoedit /etc/whonix_firewall.d/50_user.conf
3. Add the external and internal network interface names.
In the example below, replace eth0 and eth1 with the respective (actual) external and internal network interface names.
EXT_IF="eth0" INT_IF="eth1"
Save the file.
4. Edit the network interfaces file.
- Manually edit
/etc/network/interfaces.d/30_non-qubes-whonix.
Open file /etc/network/interfaces.d/30_non-qubes-whonix in an editor with administrative ("root") rights.
1 Select your platform.
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand.
3 Open the file with root rights.
sudoedit /etc/network/interfaces.d/30_non-qubes-whonix
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand. - Template requirement: When using Qubes-Whonix, this must be done inside the Template.
3 Open the file with root rights.
sudoedit /etc/network/interfaces.d/30_non-qubes-whonix
4 Notes.
- Shut down Template: After applying this change, shut down the Template.
- Restart App Qubes: All App Qubes based on the Template need to be restarted if they were already running.
- Qubes persistence: See also Qubes Persistence

- General procedure: This is a general procedure required for Qubes and is unspecific to Qubes-Whonix.
2 Notes.
- Example only: This is just an example. Other tools could achieve the same goal.
- Troubleshooting and alternatives: If this example does not work for you, or if you are not using Whonix, please refer to Open File with Root Rights.
3 Open the file with root rights.
sudoedit /etc/network/interfaces.d/30_non-qubes-whonix
Replace the interface names and save the file.
5. Create a uwtwrapper drop-in configuration snippet. [33]
- Do not edit
/uwt/usr/lib/uwtwrapper. - Instead, create a drop-in config snippet here:
/etc/uwt.d/50_user.conf.
Open file /etc/uwt.d/50_user.conf in an editor with administrative ("root") rights.
1 Select your platform.
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand.
3 Open the file with root rights.
sudoedit /etc/uwt.d/50_user.conf
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand. - Template requirement: When using Qubes-Whonix, this must be done inside the Template.
3 Open the file with root rights.
sudoedit /etc/uwt.d/50_user.conf
4 Notes.
- Shut down Template: After applying this change, shut down the Template.
- Restart App Qubes: All App Qubes based on the Template need to be restarted if they were already running.
- Qubes persistence: See also Qubes Persistence

- General procedure: This is a general procedure required for Qubes and is unspecific to Qubes-Whonix.
2 Notes.
- Example only: This is just an example. Other tools could achieve the same goal.
- Troubleshooting and alternatives: If this example does not work for you, or if you are not using Whonix, please refer to Open File with Root Rights.
3 Open the file with root rights.
sudoedit /etc/uwt.d/50_user.conf
6. Add the external and internal network interface names.
In the example below, replace the eth0 interface name.
bindp_interface="eth0"
Save the file.
7. Optional: Edit the leaktest file.
This step is not important, but /usr/bin/leaktest can be manually edited as per previous steps.
Open file /usr/bin/leaktest in an editor with administrative ("root") rights.
1 Select your platform.
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand.
3 Open the file with root rights.
sudoedit /usr/bin/leaktest
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand. - Template requirement: When using Qubes-Whonix, this must be done inside the Template.
3 Open the file with root rights.
sudoedit /usr/bin/leaktest
4 Notes.
- Shut down Template: After applying this change, shut down the Template.
- Restart App Qubes: All App Qubes based on the Template need to be restarted if they were already running.
- Qubes persistence: See also Qubes Persistence

- General procedure: This is a general procedure required for Qubes and is unspecific to Qubes-Whonix.
2 Notes.
- Example only: This is just an example. Other tools could achieve the same goal.
- Troubleshooting and alternatives: If this example does not work for you, or if you are not using Whonix, please refer to Open File with Root Rights.
3 Open the file with root rights.
sudoedit /usr/bin/leaktest
Make necessary changes and save the file.
8. Edit the systemcheck network interfaces file.
- Manually edit
/usr/lib/systemcheck/check_network_interfaces.bsh. - This will break when systemcheck is upgraded, meaning it needs to be edited again. This is configurable in Whonix 14 and above so the setting survives systemcheck upgrades.
Open file /usr/lib/systemcheck/check_network_interfaces.bsh in an editor with administrative ("root") rights.
1 Select your platform.
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand.
3 Open the file with root rights.
sudoedit /usr/lib/systemcheck/check_network_interfaces.bsh
2 Notes.
- Sudoedit guidance: See Open File with Root Rights
 for details on why using
for details on why using sudoeditimproves security and how to use it. - Editor requirement: Close Featherpad (or the chosen text editor) before running the
sudoeditcommand. - Template requirement: When using Qubes-Whonix, this must be done inside the Template.
3 Open the file with root rights.
sudoedit /usr/lib/systemcheck/check_network_interfaces.bsh
4 Notes.
- Shut down Template: After applying this change, shut down the Template.
- Restart App Qubes: All App Qubes based on the Template need to be restarted if they were already running.
- Qubes persistence: See also Qubes Persistence

- General procedure: This is a general procedure required for Qubes and is unspecific to Qubes-Whonix.
2 Notes.
- Example only: This is just an example. Other tools could achieve the same goal.
- Troubleshooting and alternatives: If this example does not work for you, or if you are not using Whonix, please refer to Open File with Root Rights.
3 Open the file with root rights.
sudoedit /usr/lib/systemcheck/check_network_interfaces.bsh
Make necessary changes and save the file.
9. Create a sudoers drop-in configuration snippet.
- Do not edit
/etc/sudoers.d/systemcheck. - Instead, create a drop-in config snippet here:
/etc/sudoers.d/systemcheck-user.
Use any preferred editor.
sudo EDITOR=nano visudo -f /etc/sudoers.d/systemcheck-user
10. Add the external and internal network interface names.
In the example below, replace the eth0 and eth1 interface names.
systemcheck ALL=NOPASSWD: /sbin/ifconfig eth0 systemcheck ALL=NOPASSWD: /sbin/ifconfig eth1
Save the file.
11. Edit the onion-grater configuration file.
- Manually edit
/usr/lib/systemd/system/onion-grater.service.d/30_cpfpy.conf. - Systemd may fail to start
onion-graterif this file is not configured properly. - As per previous steps, replace any interface names with your corresponding interface names and save the file.
TODO: it is better to use a drop-in /usr/lib/systemd/system/onion-grater.service.d/50_user.conf file; see Configuration Files.
12. Restart onion-grater.service and confirm active status.
systemctl restart onion-grater.service systemctl status onion-grater.service
Minor Issues
[edit]Most configuration files work well inside VMs and on hardware. Minor issues such as deactivating powersaving, passwordless reboot, shutdown and so on are only recommended for VMs. They can be easily commented out by putting a hash # in front of them. Since they are marked, use grep to locate them.
grep -r VMONLY* *
Run Build Script
[edit]It is recommended to create a log of the build process by redirecting all the output to a log file. Be aware that by doing so no build progress will appear on the screen -- instead a text log file will be created in the home folder.
./derivative-maker --flavor whonix-gateway-lxqt --target root --build >> ~/log-phyiso 2>&1
To optionally watch the progress, open a second virtual console and type.
tail -f ~/log-phyiso
Use the following command to avoid creating a log of the build process; the build progress will then appear on screen. Note this is unrecommended because if anything goes wrong during the build, it is harder to pinpoint the exact error without a log file.
./derivative-maker --flavor whonix-gateway --target root --build
Final Steps
[edit]Reboot.
sudo reboot
Login as new user user. (If you didn't install as user user, the old user and home folder will still exist.)
Done.
Cleanup
[edit]Remove temporary files.
Warning: This command will run git clean -d --force --force in Whonix's main source code folder![]()
(
~/derivative-maker) as well as in all subfolders of the Whonix packages folder![]()
(
~/derivative-maker/packages). This means if any files were purposefully added to any of these folders that have not been committed to git, these will be deleted. [35]
./help-steps/cleanup-files
Raspberry Pi
[edit]See Raspberry Pi.
Unrecommended: In a VM
[edit]1. Install a new operating system.
- It is advisable to install a new operating system just for hosting the Whonix-Gateway VM.
- Any operating system that can run VirtualBox works, but an open source system is preferable.
2. Download the Whonix-Gateway image. [36]
3. Configure networking.
- Adapter 1 can be set up as a NAT network.
- Adapter 2 must either:
- Be set to NAT as well -- but ports must be forwarded from the host to the guest; or
- It is much simpler to use bridged networking and set it to the second physical interface (the one that goes into the isolated network/point to point ethernet); see NAT vs Bridging below.
4. Note the following warnings.
- This configuration is not recommended unless Tor must be run through an unsupported 3G/4G/5G modem and a third physical device is unaffordable.
- Using NAT for a virtualized Whonix-Gateway requires setting up port forwarding in VirtualBox. Using a bridged network may be easier, but then the router may see the gateway MAC address which identifies as Whonix-Gateway. [37]
How-to: Install Whonix-Workstation
[edit]Recommended: In a VM
[edit]First Steps
[edit]- Install and update the host operating system. It can be any operating system that is capable of running VirtualBox, but be aware of Transparent Proxy Leaks

. Windows or other commercial proprietary systems are not recommended.
- Download the Whonix-Workstation image. [38]
- If the physical network between Whonix-Gateway and a router uses 10.152.152.* then review and edit all shell scripts and switch the internal network to something else! [39]
Host Network Adapter
[edit]Configure the host to use a static IP configuration.
## {{project_name_workstation_short}}
## /etc/network/interfaces for the host,
## when using Physical Isolation,
## with {{project_name_workstation_short}} in a VM.
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
## Increment last octet of address
## on optional additional hosts.
address 10.152.152.11
netmask 255.255.192.0
gateway 10.152.152.10
#pre-up /usr/bin/whonix_firewall
## Out commented.
## For what do we require the network and broadcast
## instances anyway?
#network 10.152.152.0
#broadcast 10.152.152.255
#auto eth0
#iface eth0 inet dhcp
## end of /etc/network/interfaces
If the physical network between Whonix-Gateway and a router uses 10.152.152.*, then review and edit all /etc/network/interfaces.
NAT vs Bridging
[edit]In the default Whonix VirtualBox image, the network adapter setting for Adapter 1 (eth0) is set to internal network and will therefore not work out of the box. There are two ways to fix this: NAT (recommended) or using a bridged network (unrecommended).
Recommended: NAT
[edit]To use NAT, edit /etc/network/interfaces in Whonix-Workstation to utilize either DHCP (easier, shown in the example below) or a static IP for VirtualBox NAT.
sudoedit /etc/network/interfaces
Replace it with.
## {{project_name_workstation_short}}
## /etc/network/interfaces in a VM
## when using Physical Isolation.
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet dhcp
## end of /etc/network/interfaces
Unrecommended: Bridged Network
[edit]If bridged networking is configured, then everything should work by default. [40] The reason is Whonix-Workstation can see the MAC address of whatever network adapter it is connected to.
For this reason it is recommended to change the MAC address for both the Workstation host and the Whonix-Gateway; see Changing MAC Addresses.
Macvtap on KVM
[edit]Change the network source of the ethernet nic to "macvtap" and the source mode to "passthrough". Be aware that you cannot use networking on the host anymore.
Attach a USB-ethernet Adapter to the VM
[edit]Remove the network adapter from the VM and instead attach a USB-ethernet adapter to the host and redirect it to the VM.
Unrecommended: On Hardware
[edit]Installing Whonix-Workstation on hardware without using a VM is recommended against, because hardware serials are visible to Whonix-Workstation.
The instructions are very similar, if not identical, to those in the How-to: Install Whonix-Gateway - Recommended: On Hardware section. The only difference is replacing --flavor whonix-gateway with --flavor whonix-workstation in relevant steps.
Expected Build Warnings
[edit]Post-installation Advice
[edit]Stay Tuned
[edit]It is absolutely crucial to subscribe to and read the latest Whonix news category 'important-news' to stay in touch with ongoing developments. This way users benefit from notifications concerning important security advisories, potential upgrade issues and improved releases which address identified issues, like those affecting the updater or other core elements.
See Stay Tuned for further information.
Extra Packages for Better Hardware Support
[edit]Some packages for bare metal could be missing. Below is an incomplete list of packages, which may or may not be useful for better hardware support. [41]
xorg xserver-xorg-input-all xserver-xorg-input-wacom xserver-xorg-input-geode xserver-xorg-input-vmmouse xserver-xephyr xserver-xorg-input-* xserver-xorg-* acpi-support-base acpid acpi discover discover-modprobe discover-data hwdata mdetect apt-cache show task-desktop apt-cache show task-kde-desktop apt-cache show task-laptop
If you have EFI bios.
grub-efi-amd64
To compile a more complete list, install Debian (with LXQt) on bare metal using the regular Debian installer medium. Then compare the package list against those installed in Whonix.
- diff "dpkg -l" with Whonix
- diff "sudo lsmod" with Whonix
- contribute the findings
- See also: Debian: HardwareAutodetection

Troubleshooting
[edit]- Slow network speed: see (SOLVED) network speed/stability (7.7.8.9 GW, physically isolated)

in the forum. In this case the WiFi driver was implicated.
- No connection between Whonix-Gateway and Whonix-Workstation: see Testers-wanted! Whonix 8 Release candidate #1 Whonix 7.7.8.6

in the forum. It may relate to Auto-MDIX

.
Known Bugs
[edit]To learn about known bugs affecting all platforms, see here. Refer to the issue tracker for a list of all all open issues affecting Whonix.
Security and Support Status
[edit]Currently there is no dedicated contributor for Whonix physical isolation. This configuration is a remnant from earlier times when no other supported platforms were available. Despite this reality, the setup and instructions are still functional and a small percentage of the Whonix user population relies upon it.
Lead Whonix developer, Patrick Schleizer, has shifted his focus to Qubes-Whonix, but grave security issues are unlikely due to the Whonix design. Unfortunately there are no Whonix contributors testing Whonix physical isolation. As a consequence, no progress on the Whonix Physical Isolation development task list![]()
should be expected. Until this situation changes the supported platforms table will continue to list physical isolation's security status as "experimental".
Help Wanted
[edit]- Work on the Whonix Physical Isolation development task list

(this is an incomplete list).
- Become a Whonix Physical Isolation contributor so the Security and Support Status can be improved.
Footnotes / References
[edit]- ↑
Rationale for Change from Default Password changeme to Empty Default Password

- ↑ Alternatively an ordinary, completely isolated, LAN behind the Whonix-Gateway™ can be set up.
- ↑ This refers to staying anonymous while building Whonix from source code. Since building Whonix requires a unique selection of software to be downloaded, the ISP can likely guess that a user is building Whonix.
- ↑ Due to the lack of an ethernet interface this is a difficult configuration and beyond the scope of the Whonix documentation. However, as a tip some (after market) firmwares support USB-host. This makes it possible to plug USB devices into your phone, such as an USB ethernet card. For example, some rooted Android smartphones can install
 Debian Linux.
Debian Linux.
- ↑ A contributor or maintainer is required, see: Whonix - Raspberry Pi

development thread.
- ↑ For example, something like OpenWRT

.
- ↑ The other one may be either an Anonymous Mobile Modem, an Anonymous WiFi Adapter, or another ethernet or WiFi device connected to the modem/router.
- ↑ Theoretically any operating system that supports iptables or pf (packet filter) could be used. Advanced users who do not want to utilize Debian need to edit the source code. This is easy for Debian derivatives, but much more difficult for other distributions such as *BSD. In any case, the operating system choice does not really matter because this system is only used for running Tor. A cheap plug computer like the Raspberry Pi, or the hardware used by Torouter would be sufficient.
- ↑ If wire connections are not configured, isolation and security is significantly weakened. If the Whonix-Workstation were infected, it could jump onto another network and start leaking information.
- ↑ Any operating system can be used, but this is not recommended! If this advice is ignored, read the following Transparent Proxy Leaks

warning, especially for Windows.
- ↑ Either Download the image or build it from source code.
- ↑ A generic VM image cannot leak identifying hardware serial numbers or unique software fingerprints via software updates.
- ↑ This ensures the VM client has the latest security features and most secure configurations, for example stream isolation to protect against identity correlation through circuit sharing, HexChat IRC hardening, Whonix protocol leak protection and fingerprinting protection, and so on.
- ↑ The build scripts can be adapted to run on other *NIX systems, but they currently assume
aptandgrml-debootstrapare available. - ↑
Parameter
-is required to set the correct paths to/usr/sbin. https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=833256
- ↑ Other methods are possible.
- ↑ Usability. Otherwise after installation is complete, user might not be able to login. Needs further testing if still required. Can be avoided for remote servers.
- ↑ This should occur by default.
- ↑ Full disk encryption (FDE) is recommended if planning to use physical isolation or the installation as the main system.
- ↑ It takes a few minutes for the base system installation to finish.
- ↑ Extra packages are not required, so do not select a mirror; "Go back".
- ↑ Select "No thanks".
- ↑ Using the space bar.
- ↑ This yields ~90 bits of entropy against classical computing attacks. To protect against hypothetical quantum computer attacks that halve the key search space, utilize a 14-word diceware passphrase.
- ↑ This section previously recommended a passphrase of at least 26 characters, including symbols.
- ↑ TODO: check whether this step is still required.
- ↑
gitis needed to obtain the source code. Alternatively, a git tag can be downloaded as an archive using a (torified) browser: https://github.com/Whonix/derivative-maker/tags
- ↑
Optional
gitparameters:--depth=1: Speeds up the download by fetching only the latest commit.--branch 18.1.4.2-developers-only: Convenience. Checks out the specified tag or branch directly.--jobs=4: Speeds up fetching submodules.--recurse-submodules --shallow-submodules: Ensures all required submodules are fetched efficiently.
gitusers may omit any of these optional parameters. - ↑
Alternatively, this can be achieved in several steps. This may be useful if network issues arise.
- Over HTTPS:
- git clone --depth=1 --branch 18.1.4.2-developers-only --jobs=4 --recurse-submodules --shallow-submodules https://github.com/Whonix/derivative-maker.git
- Over SSH:
- Might work better over slow or unstable networks but requires a GitHub account and a configured SSH public key at GitHub. See footnote [A] below.
- git clone --depth=1 --branch 18.1.4.2-developers-only git@github.com:Whonix/derivative-maker.git
[A] GitHub SSH public key setup.
1 Create an SSH public key.
See SSH.
2 View your SSH public key.
cat ~/.ssh/id_ed25519.pub
3 Copy the SSH public key.
4 Paste the SSH public key into your GitHub account.
- Over HTTPS:
- ↑ 30.0 30.1
Delete the
derivative-makersource code folder and retry.sudo rm -r derivative-maker
- ↑ As defined by TUF: Attacks and Weaknesses:
- ↑
It is advisable to verify the signature of the git commit as well. By convention, git tags should point to signed git commits. Beginning from git tag 9.6 and above. (forum discussion

)
- ↑ This is required for Whonix-Workstation in Whonix 14 and above.
- ↑ whonix-gw-network-conf

ships a file
/etc/network/interfaces.d/30_non-qubes-whonix
. Normally it should not conflict with
/etc/network/interfaces. If it does, consider:- removing source-directory
/etc/network/interfaces.dfrom/etc/network/interfaces(if there are no other files in the/etc/network/interfaces.dfolder); or - moving
/etc/network/interfaces.d/30_non-qubes-whonixout of the way. (sudo mv /etc/network/interfaces.d/30_non-qubes-whonix ~/)
- removing source-directory
- ↑ https://github.com/Whonix/derivative-maker/blob/master/help-steps/cleanup-files

- ↑ Or build it from source code.
- ↑ This is not a concern in home networks, but is a risk in untrusted networks or when using a modem to connect.
- ↑ Or build it from source code.
- ↑ TODO: check whether this step is still required.
- ↑ At least it should work, although it is untested by developers.
- ↑ These are suggestions only and individual users may need to undertake further research in their personal circumstances.

We believe security software like Whonix needs to remain open source and independent. Would you help sustain and grow the project? Learn more about our 13 year success story and maybe DONATE!